One of the main advantages of cheap wireless modules is that they get used in consumer electronics, so if you know what’s being used you can build your own compatible hardware. While investigating the RF interface used in a series of cheap “smart” solar inverters [Aaron Christophel], created an Arduino library to receive inverter telemetry using a $2 RF module. See the demonstration after the break.
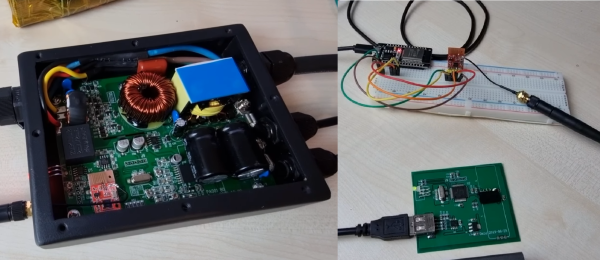
[Aaron] bought the inverter and ~40 euro USB “Data Box” that allows the user to wirelessly monitor the status of the inverter. Upon opening the two units, he found that they used LC12S 2.4Ghz modules, which create a wireless UART link. With a bit of reverse engineering, he was able to figure out the settings for the RF modules and the serial commands required to request the status of the inverter. He doesn’t delve into the possible security implications, but there doesn’t appear to be any form of encryption in the link. It should be possible for anyone with a module to sniff the messages, extract the ID of the inverter, and hijack the link. Just knowing the status of the inverter shouldn’t be all that dangerous, but he doesn’t mention what other commands can be sent to the module. Any others could have more severe implications.
Sniffing the wireless signal flashing through the air around us is a regular topic here on Hackaday. From testing the security of WiFi networks with an ESP32 to monitoring SpaceX launches with an SDR, the possibilities are infinite.