Taking his digital information into the real-world, [Davide Gironi] has built his own note transcriber from a point-of-sale receipt printer and an ESP8266.
You’ve seen these receipt printers at the order window of restaurants. A server puts in an order from any of the machines throughout the restaurant and a paper summary spits out for the chef line to start in on (and even cuts itself off from the roll). Why shouldn’t we have this convenience in our own lives?
The printer communicates using a variant of the Epson Standard Code for Printers, for which [Davide] has written a library and thankfully shared the code. Adding an ESP8266 using a couple voltage regulators and some passive components makes this wireless, except for power. It has all the fun bells and whistles to set up the WiFi credentials and once running, just push the button on the base and it’ll spit out your data.
But wait, where is that data coming from? The web-based settings page lets you configure a URI to the RESTful source of your choosing. (XKCD has one, don’t they?) It also lets you configure header, footer, error messages, and of course your company hacker logo.
One of our favorite receipt-printer moments was when Hackaday editor of yore [Eliot Phillips] brought a selfie receipt printer to Supercon. We couldn’t find any pictures of that one, so we’ll leave you with the excellent hack [Sam Zeloof] pulled off by cramming one of these into a Polaroid camera.
Continue reading “ESP8266-Powered Receipt Printer Puts RESTful API On Dead Trees”


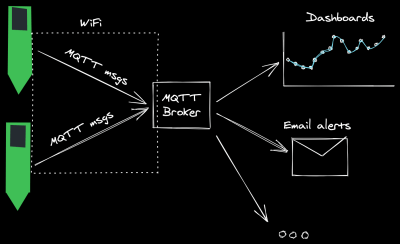
 [rbaron] has shared a string of wireless hacks,
[rbaron] has shared a string of wireless hacks,