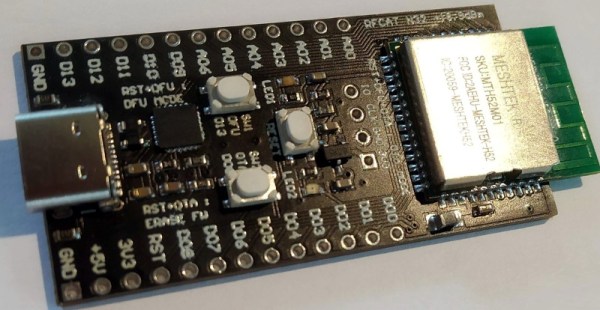
Have you ever come across an interesting chip or component that you wanted to experiment with, only to find that there doesn’t seem to be a development board for it? Spinning up your own board is a lot easier today than it has been in the past, but it’s still a bit of a hassle to do it just for your own personal use. This is why [Nikolaj Andersson Nielsen] has decided to release RFCat, his custom long-range Bluetooth development board, onto the community.
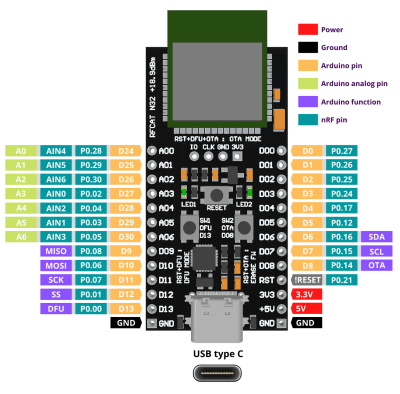 The board is based around a module from MeshTek that’s essentially an amplified version of the Nordic nRF52832. According to [Nikolaj], this gives the module 30 times the transmit power of the base model chip.
The board is based around a module from MeshTek that’s essentially an amplified version of the Nordic nRF52832. According to [Nikolaj], this gives the module 30 times the transmit power of the base model chip.
RFCat is compatible with the Arduino IDE and uses the Adafruit nRF52 bootloader, making it easy to write your own code to take advantage of all this new-found power. Primarily you’d be programming the board over USB-C, but it also supports Serial Wire Debug (SWD) and over-the-air updates that can be triggered with a physical push button on the device.
If you want to get an RFCat of your own, it’s available on Tindie now. The amplified modules were originally intended for building Bluetooth mesh networks, but we’re sure there are other interesting applications out there just waiting to be discovered.
Continue reading “Bluetooth Development Board Goes The Distance”