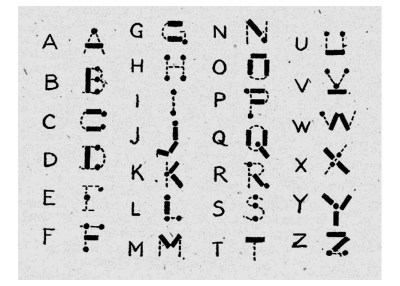
It might seem antiquated, but Morse code still has a number of advantages compared to other modes of communication, especially over radio waves. It’s low bandwidth compared to voice or even text, and can be discerned against background noise even at extremely low signal strengths. Not every regulatory agency requires amateur operators to learn Morse any more, but for those that do it can be a challenge, so [Cristiano Monteiro] built this clock to help get some practice.
 The project is based around his favorite microcontroller, the PIC16F1827, and uses a DS1307 to keep track of time. A single RGB LED at the top of the project enclosure flashes the codes for hours in blue and minutes in red at the beginning of every minute, and in between flashes green for each second.
The project is based around his favorite microcontroller, the PIC16F1827, and uses a DS1307 to keep track of time. A single RGB LED at the top of the project enclosure flashes the codes for hours in blue and minutes in red at the beginning of every minute, and in between flashes green for each second.
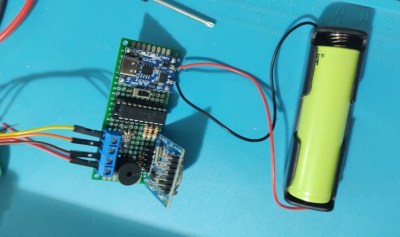
Another design goal of this build was to have it operate with as little power as possible, so with a TP4056 control board, single lithium 18650 battery, and some code optimization, [Cristiano] believes he can get around 60 days of operation between charges.
For a project to help an aspiring radio operator learn Morse, a simple build like this can go a long way. For anyone else looking to build something similar we’d note that the DS1307 has a tendency to drift fairly quickly, and something like a DS3231 or even this similar Morse code clock which uses NTP would go a long way to keeping more accurate time.