After his death, Aaron Swartz became one of the Internet’s most famous defenders of the free exchange of information, one of the most polarizing figures on the topic of intellectual property, and the most famous person that still held on to the ideals the Internet was founded on. Aaron was against DRM, fought for the users, and encouraged open access to information.
Early this year, Verso Books published the collected writings of Aaron Swartz. This eBook, according to Verso, contains ‘social DRM’, a watermarking technology that Verso estimates will, “contribute £200,000 to the publisher’s revenue in its first year.” This watermarking technology embeds uniquely identifiable personal information into individual copies of eBooks.
With a heavy sigh, you realize you do not live in the best of all possible worlds.
The Institute for Biblio-Immunology had a similar reaction to Verso Books’ watermarking technology applied to the collected writings of Aaron Swartz. In a communique released late last weekend, they cracked this watermarking scheme and released the code to remove this ‘social DRM’ from ePub files.
The watermarking technology in Aaron Swartz’s eBook comes courtesy of BooXtream, a security solution where every eBook sold is unique using advanced watermarking and personalization features. “A publication that has been BooXtreamed can be traced back to the shop and even the individual customer,” the BooXtream website claims, and stands in complete opposition to all of Aaron Swartz’s beliefs.
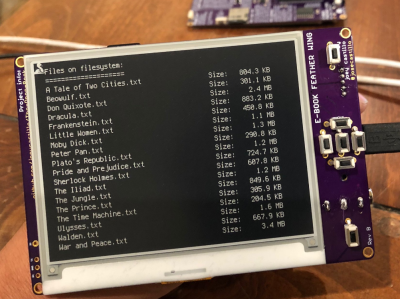
After analyzing several digital copies of Aaron Swartz’s eBook, the Institute for Biblio-Immunology is confident they have a tool that removes BooXtrem’s watermarks in EPUB eBooks. Several watermarks were found, including the very visible – Ex Libris images, disclaimer page watermarks, and footer watermarks – and the very hidden, including image metadata, filename watermarks, and timestamp fingerprints.
While the Institute believes this tool can be used to de-BooXtream all currently available ‘social DRM’ed’ eBooks, they do expect the watermarking techniques will be quickly modified. This communique from the Institute of Biblio-Immunology merely provides the background of what BooXtream does, not the prescription for the disease of ‘social DRM’. These techniques can be applied to further social DRM’ed eBooks, which, we think, is what Aaron would have done.






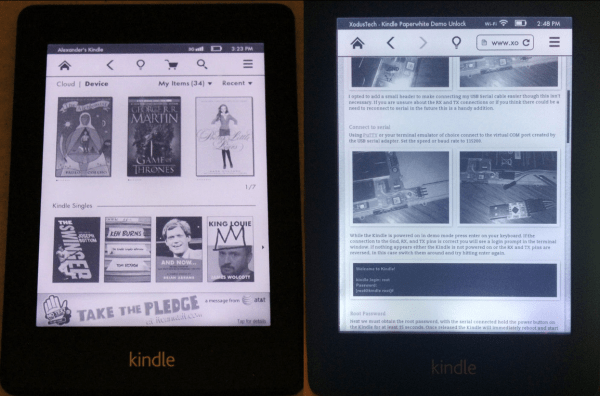
 The first step was to crack open the case and locate the serial port. [WarriorRocker] soldered a small three pin header to the pads to make it easier to work on his device as needed. He then connected the Kindle to his PC using a small serial to USB adapter. Pulling up the command prompt was as simple as running Putty and connecting to the correct COM port. If the wires are hooked up correctly, then it just takes a press of the enter key to pull up the login prompt.
The first step was to crack open the case and locate the serial port. [WarriorRocker] soldered a small three pin header to the pads to make it easier to work on his device as needed. He then connected the Kindle to his PC using a small serial to USB adapter. Pulling up the command prompt was as simple as running Putty and connecting to the correct COM port. If the wires are hooked up correctly, then it just takes a press of the enter key to pull up the login prompt.








