Everyone’s favourite IOT module, the ESP8266, is often the go-to choice for any project that needs quick and cheap control over the web. [Andi23456] wanted to control his quadcopter using the luxury of his mobile phone and thought permanently tethering an ESP12-E module to the quadcopter was exactly what he required.
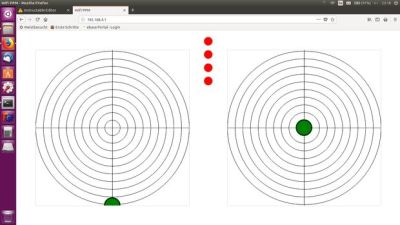
The ESP8266, really showcasing its all-round prowess, hosts both a web server for a HTML5 based joystick and a Websockets server so that a client, such as a phone, could interact with it over a fast, low latency connection. Once the ESP8266 receives the input, it uses interrupts to generate the corresponding PPM (Pule Position Modulation) code which the RC receiver on the quadcopter can understand. Very cool!
What really makes this realtime(ish) control viable is Websockets, a protocol that basically allows you to flexibly exchange data over an “upgraded” HTTP connection without having to lug around headers each time you communicate. If you haven’t heard of Websockets you really should look really check out this library or even watch this video to see what you can achieve.