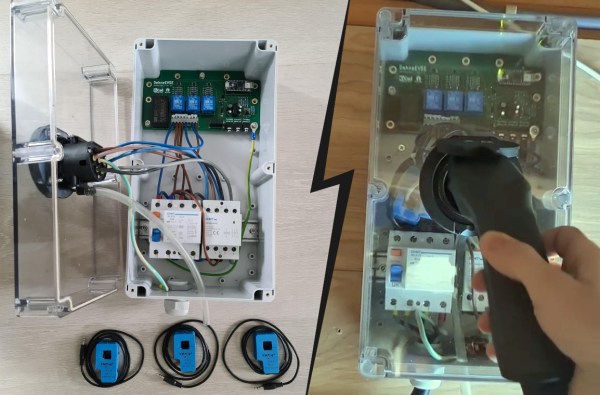
QR codes are something that we all take for granted in this day and age. There are even a million apps to create your own QR codes, but what if you want to make a barcode? How about making a specific kind of barcode that follows UPC-E, CODE 39, or even the infamous… CODABAR? Well, it might be more difficult to find a single app that can handle all those different standards. Using “yet-another-web-app”, Barcode Tool – Generator & Scanner, you can rid these worries, created by [Ricardo de Azambuja].
When going to [Ricardo]’s simple application, you will find a straightforward interface that allows you to make far more different strips and square patterns than you’ve ever imagined. Of course, starting with the common QR code, you can create custom overlaid codes like many other QR generators. More uniquely, there are options for any barcode under the sun to help organize your hacker workspace. If you don’t want to download an app to scan the codes, you can even use the included scanner function.
If you want to use the web app, you can find it here! In-depth solutions to rather simple problems are something we strive to provide here at Hackaday, and this project is no exception. However, if you want something more physical, check out this specialized outdoor city cooking station.