While things like the Arduino platform certainly opened up the gates of microcontroller programming to a much wider audience, it can also be limiting in some ways. The Arduino IDE, for example, abstracts away plenty of the underlying machinations of the hardware, and the vast amount of libraries can contribute to this effect as well. It’s not a problem if you just need a project to get up and running, in fact, that’s one of its greatest strengths. But for understanding the underlying hardware we’d recommend taking a look at something like this video series on the STM32 platform.
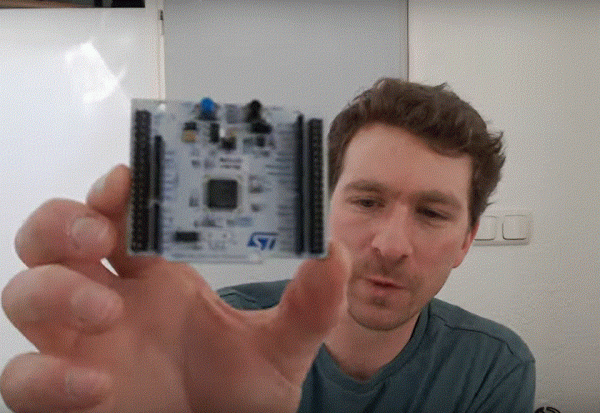
The series comes to us from [Francis Stokes] of Low Byte Productions who has produced eighteen videos for working with the STM32 Cortex-M4 microcontroller. The videos start by getting a developer environment up and blinking LEDs, and then move on to using peripherals for more complex tasks. The project then moves on to more advanced topics and divides into two parts, the development of an application and also a bootloader. The bootloader begins relatively simply, and then goes on to get more and more features built into it. It eventually can validate and update firmware, and includes cryptographic signing (although [Francis] notes that you probably shouldn’t use this feature for production).
One of the primary goals for [Francis], apart from the actual coding and development, was to liven up a subject matter that is often seen as dry, which we think was accomplished quite well. A number of future videos are planned as well. But, if you’re not convinced that the STM32 platform is the correct choice for you, we did publish a feature a while back outlining a few other choices that might provide some other options to consider.
Continue reading “Blinkenlights To Bootloader: A Guide To STM32 Development”