So you say you missed the Great Solar Storm of 2024 along with its attendant aurora? We feel you on that; the light pollution here was too much for decent viewing, and it had been too long a day to make a drive into the deep dark of the countryside survivable. But fear not — the sunspot that raised all the ruckus back at the beginning of May has survived the trip across the far side of the sun and will reappear in early June, mostly intact and ready for business. At least sunspot AR3664 seems like it’s still a force to be reckoned with, having cooked off an X-class flare last Tuesday just as it was coming around from the other side of the Sun. Whether 3664 will be able to stir up another G5 geomagnetic storm remains to be seen, but since it fired off an X-12 flare while it was around the backside, you never know. Your best bet to stay informed in these trying times is the indispensable Dr. Tamitha Skov.
hype8 Articles
Bots That Snag The Hottest Fashion While Breaking Social Trust In Commerce
Scarcity on the Internet is the siren song of bot writers. Maybe you’ve lost an eBay bid in the last milliseconds, or missed out on a hacker con when tickets sold out in under a minute — your corporeal self has been outperformed by a bot. But maybe you didn’t know bots are on a buying frenzy in the hyped-up world of fashion. From limited-run sneakers to anything with the word Supreme printed on it, people who will not accept any substitute in wearing the rarest and most sought after are turning to resellers who use bots to snag unobtanium items and profit on the secondary market.
At DEF CON 27 [FinalPhoenix] took the stage to share her adventures in writing bots and uncovering a world that buys and sells purchasing automation, forming groups much like cryptocurrency mining pools to generate leads on when the latest fashion is about to drop. This is no small market either. If your bots are leet enough, you can make a ton of cash. Let’s take a look at what it takes to write a bot, and at the bots-for-sale economy that has grown up around these concepts.
The internet is built with bots in mind and we have Google to thank for this. Their major innovation was moving us off of a curated internet to one that is machine crawled. Everyone wants good Google juice and that means building a site that is friendly to the Google bots that crawl and index the internet. This makes automation for your own purposes quite a bit easier. Namely, the monitor-bots that are used to detect when a retailer has the latest in stock. [FinalPhoenix] demonstrated a simple script that grabs the XML site map, parsing it for newly in-stock items, flagging them when found. But here’s the killer — if your monitor bot is a good one, you can turn it into a discord channel and sell subscriptions to others playing the reseller game, to the tune of $15-30 a month per subscriber.
Once your bot reports stock, the race is on to buy it before anyone else can. For this, you could use the APIs of the site, but that’s time-consuming and a lot easier for retailers to detect and block bot usage. For this part of her botting tools [FinalPhoenix] likes to use web-based bots that go through a browser framework like Chromium and allow obfuscation techniques like scrolling, clicking other items, random pauses, and other simple-minded actions that make your bot appear to be only human. In the examples for this talk, the Puppeteer framework was used for this purpose. In the end, the main role of this part of the bot is to use a verified account to complete the purchase as fast as robotically possible, which is why they’re called buy-bots. Retailers do have some tricks to combat these web-based attacks like adding secret keys in the DOM that need to be sent with the next post, but these are easy to discover and incorporate into the scripts.
This raises up another interesting part of the scheme, the verified accounts. For the best chance at profit, you need multiple accounts, each used just one time to avoid your buy-bot being detected by the retailer. For this, [FinalPHoenix] turns to services that sell accounts in packages of 500-10,000 and cost around just $5-10 per batch.
But wait, here’s where it gets really wild as recursion takes hold. Yes, these buy-bots are for sale (from sites like AIO Bot and usually around $300-1500), but they’re sold in limited quantities so that it’s harder for retailers to notice and take countermeasures. Just like how the clothing was limited release and incentivized bots-wielding resellers to enter the market, there is a secondary market for the bots themselves. [FinalPhoenix] reports that reselling one of these bots can yield $1000-1500 in profit. The same principles apply, and so what we’ve ended up with is bots buying bots to buy clothes. Who knows how many levels of bot-bot transactions there are, but it certainly feels like turtles all the way down.
Bot-based high-speed trading is the real way to make major bank on the securities market. Your average hacker is shut out of that “legitimate” business, but any enterprising programmer has the option of automating whichever reseller market they find most interesting. This breaks the public trust in commerce — buying quality products from a seller connected to their production for a reasonable price. If frustrates the manufacturer, alienates the consumer, but there appears to be little in place preventing it.
One-Pixel Attack Fools Neural Networks
Deep Neural Networks can be pretty good at identifying images — almost as good as they are at attracting Silicon Valley venture capital. But they can also be fairly brittle, and a slew of research projects over the last few years have been working on making the networks’ image classification less likely to be deliberately fooled.
One particular line of attack involves adding particularly-crafted noise to an image that flips some bits in the deep dark heart of the network, and makes it see something else where no human would notice the difference. We got tipped with a YouTube video of a one-pixel attack, embedded below, where changing a single pixel in the image would fool the network. Take that robot overlords!

Or not so fast. Reading the fine-print in the cited paper paints a significantly less gloomy picture for Deep Neural Nets. First, the images in question were 32 pixels by 32 pixels to begin with, so each pixel matters, especially after it’s run through a convolution step with a few-pixel window. The networks they attacked weren’t the sharpest tools in the shed either, with somewhere around a 68% classification success rate. What this means is that the network was unsure to begin with for many of the test images — making it flip from its marginally best (correct) first choice to a second choice shouldn’t be all that hard.
This isn’t to say that this line of research, adversarial training of the networks, is bogus. The idea that making neural nets robust to small changes is important. You don’t want turtles to be misclassified as guns, for instance, or Hackaday’s own Steven Dufresne misclassified as a tobacconist. And you certainly don’t want speech recognition software to be fooled by carefully crafted background noise. But if a claim of “astonishing results” on YouTube seems too good to be true, well, maybe it is.
Thanks [kamathin] for the tip!
Don’t Get Caught Up In Blockchain Hype
It’s the story of the moment, isn’t it. As the price of Bitcoin continues on its wild and crazy rollercoaster ride, everyone’s talking about cryptocurrencies, and in almost mystical terms, about blockchains. Perhaps to be a little more accurate, we should report that they are talking about The Blockchain, a single entity which it seems is now the answer to all ills.
Of course, there is no single blockchain, instead blockchain technologies form the underpinnings of the cryptocurrency boom. Since little dollar signs seem to be buzzing around in front of everyone talking about that subject, it has attracted the attention of hordes of people with little understanding of it. APNIC have a good article aimed at those people: Don’t Get Caught Up In Blockchain Hype, which is worth a read even if you do understand blockchain technologies.
It makes the point that many large enterprises are considering investments in blockchain technologies, and lists some of the potential pitfalls that they may encounter. There may be a slight element of schadenfreude for some of the technically literate in seeing this in action, but given that such things can have consequences for those among us it’s too important to ignore.
As an analogy of a relatively clueless executive jumping on a tech-driven bandwagon, a software company of our acquaintance had a boss who decided in the heady days before the dotcom crash that the organisation would fully embrace open-source. Something to be welcomed, you might think, but given that the software in question was a commercially sensitive asset upon which all company salaries depended, it was fortunate that he listened to his developers when they explained to him exactly what open source entails.
Whether you are a blockchain savant or an uninterested bystander, it’s worth a read as you may sometime need its arguments to save someone from their own folly. If you fancy a simple example to help understand something of how blockchains work, we’ve got that covered for you.
Bitcoin coins image: Mike Cauldwell [Public domain].
Get Your Internet Out Of My Things
2014 was the year that the Internet of Things (IoT) reached the “Peak of Inflated Expectations” on the Gartner Hype Cycle. By 2015, it had only moved a tiny bit, towards the “Trough of Disillusionment”. We’re going to try to push it over the edge.
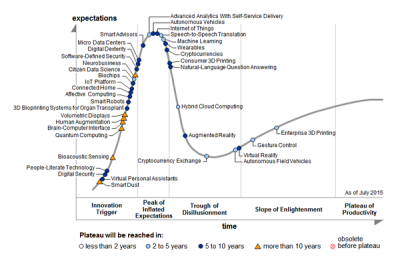 Depending on whom you ask, the IoT seems to mean that whatever the thing is, it’s got a tiny computer inside with an Internet connection and is sending or receiving data autonomously. Put a computer in your toaster and hook it up to the Internet! Your thermostat? Hook it up to the Internet!? Yoga mat? Internet! Mattress pad? To the Intertubes!
Depending on whom you ask, the IoT seems to mean that whatever the thing is, it’s got a tiny computer inside with an Internet connection and is sending or receiving data autonomously. Put a computer in your toaster and hook it up to the Internet! Your thermostat? Hook it up to the Internet!? Yoga mat? Internet! Mattress pad? To the Intertubes!
Snark aside, to get you through the phase of inflated expectations and on down into disillusionment, we’re going to use just one word: “security”. (Are you disillusioned yet? We’re personally bummed out anytime anyone says “security”. It’s a lot like saying “taxes” or “dentist’s appointment”, in that it means that we’re going to have to do something unpleasant but necessary. It’s a reality-laden buzzkill.)
“Scotty” Is More Hungry 3D-printing Fax Machine Than Teleporter
Researchers at the Hasso Plattner Institute have created “Scotty,” a so-called teleportation system. While the name is a clear homage to the famous Star Trek character, this is not the Sci-Fi teleporting you may be expecting. The system is composed of two 3D printers (they used a pair of MakerBot Replicators). The “sender” printer has a camera and built-in milling machine. It uses deconstructive scanning – taking the picture of an object’s layer, then grinding that layer down to expose the next layer – and then sends the encrypted data to a “receiver” printer with a RasPi to decrypt the data so that it can immediately print the object. The ultimate idea behind this is that there is only one object at the end of the process.
It’s a disservice describing Scotty as a teleporter. By the researchers’ definition of a teleporter, the lowly fax machine is on par with Scotty – and it doesn’t destroy the original. The researchers claim that this destructive-reconstuctive method preserves the uniqueness of a given object, as long as any sentimentality. We can agree with the unique aspect: the less copies of something means it retains it intrinsic value in the marketplace. The sentimentality – not so much. We’ve all had a moment in our lives where a treasured item of ours, worthless to everyone else, was destroyed. Either we’d get a replacement or someone else would give us one to silence our wailing, but it wasn’t quite the same. If you could clone your dead pet, subconsciously you’d know it’s not going to be the same Fluffy. It’s that exact thing, atoms and all, that has the emotional attachment. Trying to push that psychological perspective onto Scotty’s purpose is irksome.
Continue reading ““Scotty” Is More Hungry 3D-printing Fax Machine Than Teleporter”
Portable Large Interactive Display
[vimeo http://vimeo.com/5452585%5D
[HyPe] over at the Natural User Interface Group developed this concept as part of his Master’s Degree in Industrial Design. This suitcase sized projector and computer allows people to have a 60″ multitouch screen available wherever there is a large enough surface. The current software is designed for ad-hoc meetings about large-scale construction plans. The rolling case includes a short-throw projector and webcam. Just set it on top of your work surface, lift the lid, and it’s ready to go.
















