Unbinare is a small Belgian company at the forefront of hacking e-waste into something useful, collaborating with recycling and refurbishing companies. Reverse-engineering is a novel way to approach recycling, but it’s arguably one of the most promising ways that we are not trying at scale yet. At Hackaday Remoticon 2021, Maurits Fennis talked about Unbinare’s efforts in the field and presented us with a toolkit he has recently released as a part of his work, as well as described how his background as an artist has given him insights used to formulate foundational principles of Unbinare.
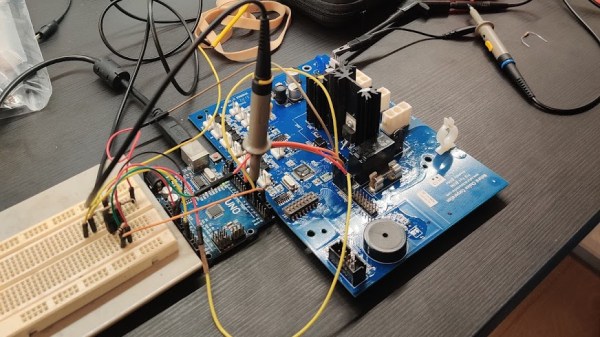
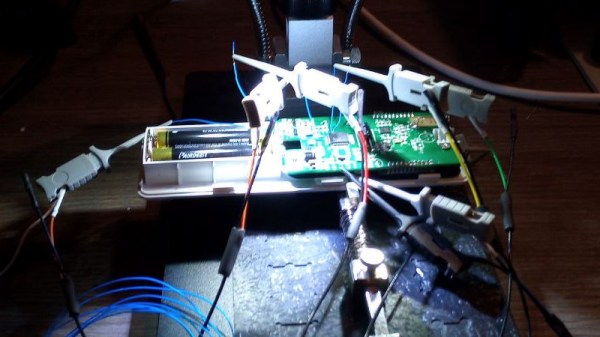
 Unbinare’s tools are designed to work in harmony with each other, a requirement for any productive reverse-engineering effort. OI!STER is a general-purpose salvaged MCU research board, with sockets to adapt to different TQFP chip sizes. This board is Maurits’s experience in reverse-engineering condensed into a universal tool, including a myriad of connectors for different programming/debugging interfaces. We don’t know the board’s full scope, but the pictures show an STM32 chip inside the TQFP socket, abundant everywhere except your online retailer of choice. Apart from all the ways to break out the pins, OI!STER has sockets for power and clock glitching, letting you target these two omnipresent Achilles’ heels with a tool like ChipWhisperer.
Unbinare’s tools are designed to work in harmony with each other, a requirement for any productive reverse-engineering effort. OI!STER is a general-purpose salvaged MCU research board, with sockets to adapt to different TQFP chip sizes. This board is Maurits’s experience in reverse-engineering condensed into a universal tool, including a myriad of connectors for different programming/debugging interfaces. We don’t know the board’s full scope, but the pictures show an STM32 chip inside the TQFP socket, abundant everywhere except your online retailer of choice. Apart from all the ways to break out the pins, OI!STER has sockets for power and clock glitching, letting you target these two omnipresent Achilles’ heels with a tool like ChipWhisperer.
Continue reading “Remoticon 2021: Unbinare Brings A Reverse-Engineering Toolkit Into Recycling”