Between smartphones and tablets, computing is becoming increasingly mobile in nature. It used to be that everyone had a desktop computer, then laptops became the norm, and now many people don’t have anything beyond their mobile device. Unless you’re the kind of person who actually needs the power and versatility offered by a “real” computer, mobile devices are simply a more convenient option to browse the web and consume content.
 But what if your needs are somewhere in the middle? You want an x86 computer and full operating system, but you also want something that’s more mobile than a tablet? If you’re like [mnt], you take an old Atom laptop that’s on its last legs and rebuild it as the Hacktop.
But what if your needs are somewhere in the middle? You want an x86 computer and full operating system, but you also want something that’s more mobile than a tablet? If you’re like [mnt], you take an old Atom laptop that’s on its last legs and rebuild it as the Hacktop.
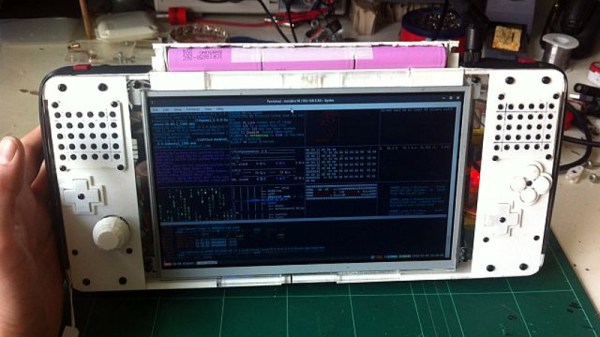
[mnt] describes the Hacktop as an “Emergency Gaming/Hacking Station”, and says he uses it everywhere he goes. Inspired by his Nintendo DSi, gaming controls are front-and-center on the Hacktop and he uses the machine to play everything from Half-Life to classic emulators.
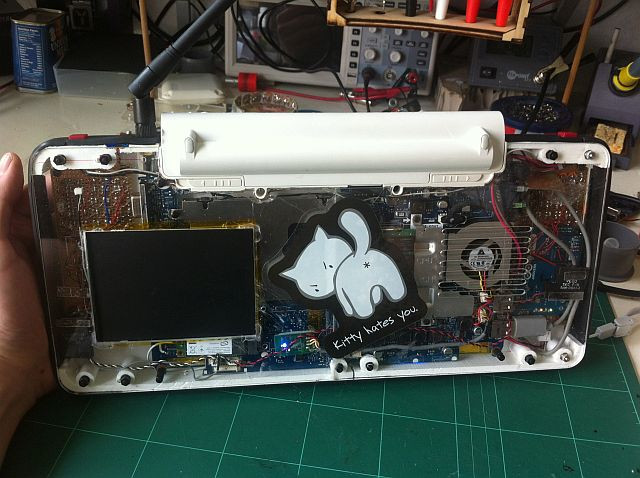
But the Hacktop is capable of more than just playing Amiga games. The hand-soldered QWERTZ keyboard can be used with his thumbs, and the D-Pad doubles as the cursor keys. There’s a laptop touch pad on the back of the case, and the ten-inch LCD display is a touch screen as well. Definitely no shortage of input devices on this thing. It’s also packing some interesting special features, such as integrated RTL-SDR and LIRC hardware for mobile exploration and experimentation. [mnt] says the nine-cell battery should keep it alive and kicking for twelve hours or so, but it of course depends on what kind of stuff he gets into while out and about.
Hackers have been building their own mobile devices for a long time, and we’re always struck by the creative approaches individuals take compared to the rather cookie-cutter world of mobile consumer technology.