As much as we’d like to have the right tools for the right job all of the time, sometimes our parts drawers have other things in mind. After all, what’s better than buying a new tool than building one yourself from things you had lying around? That’s at least what [Saulius] must have been thinking when he needed a thermometer with a digital output, but only had a dumb, but feature-rich, thermometer on hand.
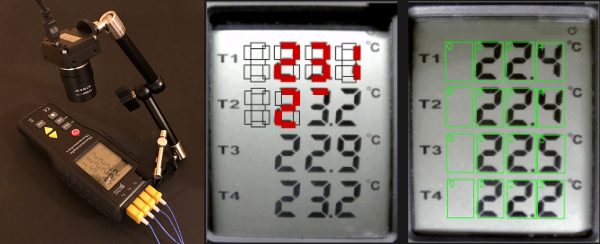
Luckily, [Saulius] had a webcam lying around as well as an old thermometer, and since the thermometer had a LCD display it was relatively straightforward to get the camera to recognize the digits in the thermometer’s display. This isn’t any old thermometer, either. It’s a four-channel thermometer with good resolution and a number of other useful features (with an obvious lack of communications abilities), so it’s not something that he could just overlook.
Once the camera was mounted to an arm and pointed at the thermometer’s screen, an algorithm running on a computer detects polygons and reports its information into a CSV file. This process is made simpler by the fact that LCD screens like this are very predictable. From there, the data is imported into LibreOffice and various charts and graphs can be made.
Although perhaps not the most elegant of hacks, sometimes you have to work with the supplies that are on hand at the time. Sometimes the tools you need are too expensive, politically dangerous, or too impractical to obtain. To that end [Saulius]’s hack is a great example of what hacks are possible with the right mindset.