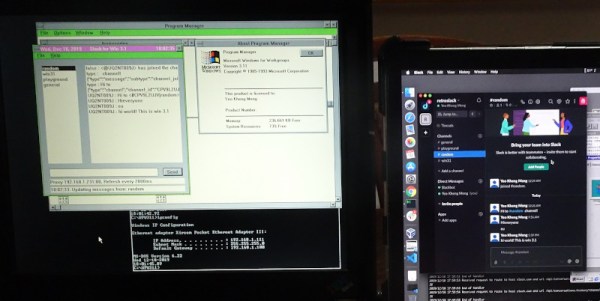
Slack is either an online collaboration tool, or a religion, depending on who you talk to. Naturally, it’s accessible across all manner of modern platforms, from Windows and MacOS to smartphones. However, some prefer to go further back. At a recent company hackathon, [Yeo Kheng Meng] decided to create a Slack client for Windows 3.1.

Programming for an older OS, in this case, Windows For Workgroups 3.11, requires setting up a viable development environment. Visual C++ 1.52 was pressed into service in this case, being the last version capable of targeting Windows 3.11. The development environment is run on a Windows 2000 virtual machine running on a Mac laptop. This was chosen for its ability to run 16-bit apps, and its Samba compatibility with both Windows 3.11 and Windows 10 and modern Macs.
There were several challenges to face along the way. Old school Windows simply isn’t capable of dealing with HTTPS, necessitating a proxy to handle the exchange of packets with Slack servers. Additionally, memory management was a hassle due to the limits of the 16-bit architecture. Thankfully, an old programming manual from the era was of great help in this regard.
At the end of the hackathon, a usable Slack client was up and running, complete with garish colors from the early Windows era. There’s a few key features missing, such as the ability to resolve user IDs, but overall, the concept works. We’ve seen [Yeo]’s work with this vintage OS before too. Video after the break.