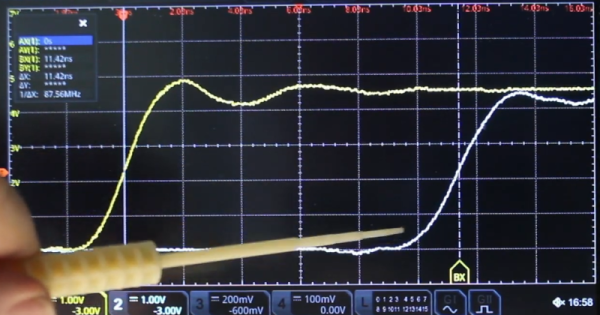
When is the speed of light not the speed of light? Of course, that’s a trick question. The speed of light may be constant, but just as sound travels at different speeds in different media, electronic signals move through transmission lines at a reduced speed. When you have a known cable, you can look up the velocity factor and use it to approximate the length of cable to have a given effective length. But what if you don’t know what kind of cable you have? [More Than Electronics] used a scope to measure it. You can see what he did in the video below.
For example, RG-8/U has a factor of 0.77. Even air isn’t exactly a factor of 1, although it is close enough that, in practice, we pretend that it is. If you wonder why it matters, consider stubs. Suppose you have a 300 MHz signal (handy because that’s 1 meter in wavelength; well, OK, pick 299.792 MHz if you prefer). If you have a quarter wavelength piece of coax shorted at one end, it will attenuate signals at 300 MHz. To understand why, picture the wave on the stub. If the close end of the stub is at 0 volts, then the other end — because it is a quarter wavelength away — must be at the maximum positive voltage or the minimum negative voltage. If either of the extremes is at the close end, then the far end must be at zero volts. That means the maximum current flows only when the signal is at 300 MHz.