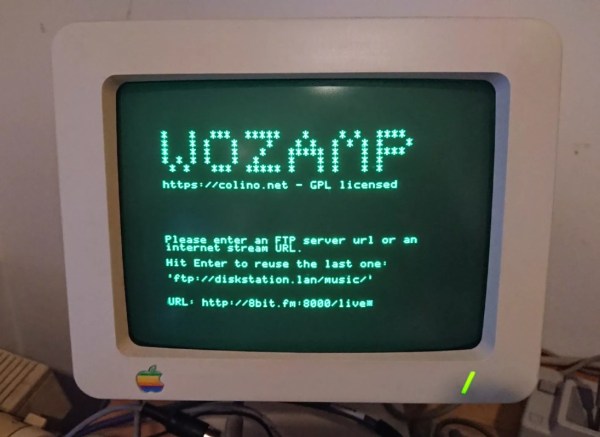
Besides obvious technological advancements, early computers built by Apple differed in a major way from their modern analogs. Rather than relying on planned obsolescence as a business model, computers like the Apple II were designed to be upgradable and long-term devices users would own for a substantially longer time than an iPhone or Macbook. With the right hardware they can even be used in the modern era as this project demonstrates by turning one into a music player.
The requirements for this build are fairly short; an Apple II with a serial card and a piece of software called surl-server which is a proxy that allows older computers to communicate over modern networks. In this case it handles transcoding and resampling with the help of a Raspberry Pi 3. With that all set up, the media player can play audio files in an FTP network share or an online web radio station. It can also display album art on the Apple II monitor and includes a VU meter that is active during playback.
Although the 11.52 kHz sampling rate and 5-bit DAC may not meet the stringent requirements of audiophile critics, it’s an impressive build for a machine of this era. In fact, the Apple II has a vibrant community still active in the retrocomputing world, with plenty of projects built for it including others related to its unique audio capabilities. And if you don’t have an original Apple II you can always get by with an FPGA instead.