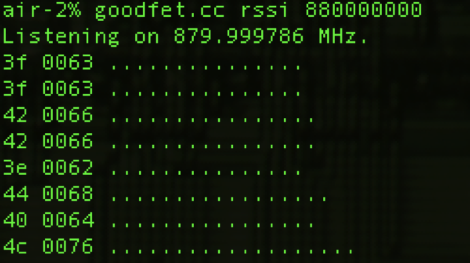
The ubiquitous presence of wireless devices combined with easy access to powerful RF development platforms makes the everyday world around us a wireless hacker’s playground. Yesterday [Travis Goodspeed] posted an article showing how goodfet.cc can be used to sniff wireless traffic and also to jam a given frequency. We’ve previously covered the work of [Travis] in pulling raw data from the IM-ME spectrum analyzer, which also uses goodfet.cc.
The Texas Instruments Chronos watch dev platform contains a C1110 chip, which among other things can provide accelerometer data from the watch to an interested sniffer. The i>clicker classroom response device (which houses a XE1203F chip) is also wide open to this, yielding juicy info about your classmates’ voting behaviour. There is still some work to be done to improve goodfet.cc, and [Travis] pays in beer–not in advance, mind you.
With products like the Chronos representing a move towards personal-area wireless networks, this sort of security hole might eventually have implications to individual privacy of, for example, biometric data–although how that might be exploited is another topic. Related to this idea is that of sniffable RFID card data. How does the increasing adoption of short-range wireless technologies affects us, both for good and bad? We invite you to share your ideas in the comments.
















