As we stand here looking at the brand-new year ahead, we find ourselves taking stock, and maybe thinking how we can all be better people in the next year. More exercise, being nicer to your neighbors, consuming more or less of this or that, depending on whether it’s healthy or un. Those are the standard fare. But what’s your hacker new year’s resolution?
Mine, this year, is to branch out into a new microcontroller family, to learn a new toolchain, and maybe to finally dip my toes into Bluetooth Low Energy. Although that last one is admittedly a stretch.
But the former is great resolution material, if you allow me. New programming tooling is always a little unpleasant to set up, but there’s also payoff at the end of the ordeal. It’s a lot like picking up a new exercise – it makes you stronger. Or course, it helps to have an application in mind, the equivalent of that suit you want to be able to fit into at the end of the diet. I’ve got one. I’ve also been out of programming in straight C for a year or so, and I’m faced with a new HAL, so there’s bound to be enough of a challenge to make it worthwhile.
Honestly, I’m looking forward to getting started, but with the usual mix of optimism, over-optimism, and mild dread. It’s the perfect setup for a resolution! What’s yours?
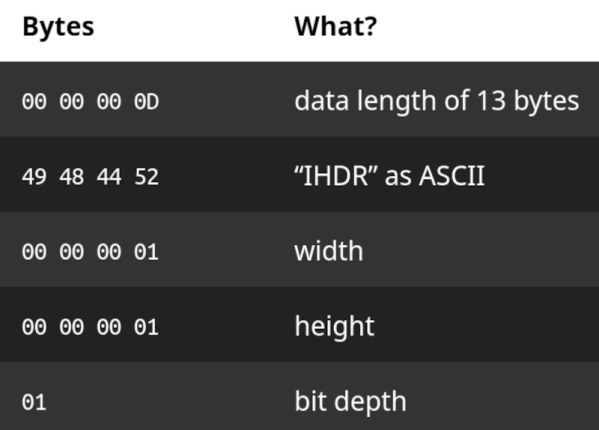
(And yes, the art is from another story, but setting up a good backup regime isn’t a bad resolution either.)