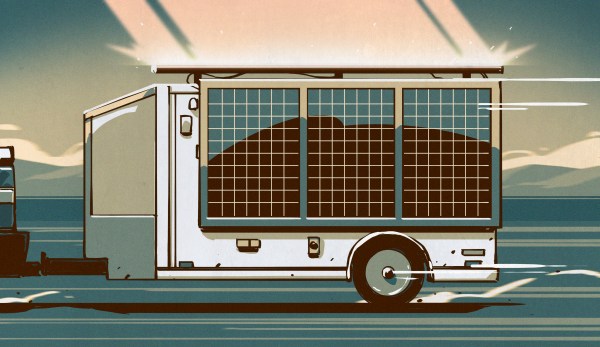
For obvious reasons, there has been a lot of interest in small-scale residential solar power systems lately. Even in my neck of the woods, where the sun doesn’t shine much from October to April, solar arrays are sprouting up on rooftops in a lot of local neighborhoods. And it’s not just here in suburbia; drive a little way out into the country or spend some time looking around in Google maps and it won’t take long to spy a sizable array of PV panels sitting in a field next to someone’s ranch house or barn.
Solar has gotten to the point where the expense of an installation is no longer a serious barrier to entry, at least if you’re willing to put in a little sweat equity and not farm the project out to a contractor. Doing it yourself requires some specialized tools and knowledge, though, over and above your standard suite of DIY skills. So, in the spirit of sharing hard-won knowledge, I decided to take the somewhat unusual step of writing up one of my personal projects, which has been in progress for a couple of years now and resulted in a solar power system that isn’t on a rooftop or a ground-mounted array at all, but rather is completely mobile: my solar trailer.
Continue reading “Sun On The Run: Diving Into Solar With A Mobile PV System”