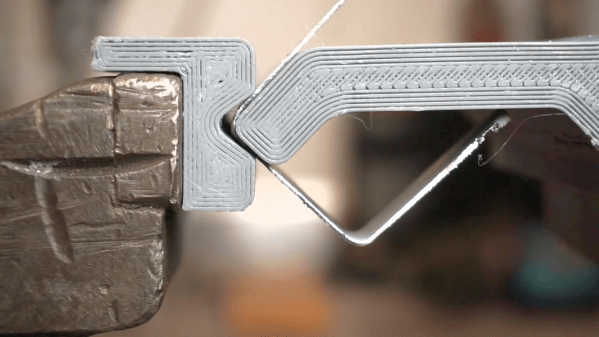
Like a number of hackers before him, [MarcelMG] was impressed with Weller’s RT soldering iron tips, but considerably less enthused about the high purchase price on the station they’re designed to go into. Inspired by similar projects, he decided to try his hand at building his own soldering station which reaps the benefits of these active tips without the sticker shock.
The station’s user interface was kept intentionally simple, with little more than a four digit LED display to show the temperature and a rotary encoder to set it. The display alternates between the current temperature and the set temperature every few seconds while the knob is being turned, and if you push it in, the set temperature will be saved as the default for next time.
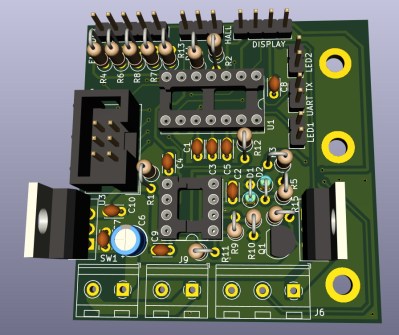 [MarcelMG] also included a feature that drops the iron’s temperature when it’s sitting in the holder, reducing tip wear and energy consumption. He originally planned on using a Hall effect sensor to detect when the iron was holstered without needing to physically interface with it, but in the end he realized the easiest approach was to simply connect one of the input pins on the microcontroller to the metal holder. Since the tip is grounded, he could easily detect if it was in place with a couple lines of code.
[MarcelMG] also included a feature that drops the iron’s temperature when it’s sitting in the holder, reducing tip wear and energy consumption. He originally planned on using a Hall effect sensor to detect when the iron was holstered without needing to physically interface with it, but in the end he realized the easiest approach was to simply connect one of the input pins on the microcontroller to the metal holder. Since the tip is grounded, he could easily detect if it was in place with a couple lines of code.
Speaking of which, the station is powered by an ATtiny24A with firmware written in C using the Atmel Studio IDE. [MarcelMG] mentions that the limited storage on the 24A was a bit of a challenge to work around, and suggests that anyone looking to follow in his footsteps uses something with a bit more flash under the hood. The LED display is a very common TM1637 type, the rotary encoder was salvaged from a radio, and the power supply was from an old laptop. All told, this looks like a very economical build.
Depending on your needs, a DIY soldering station can either have features to rival the commercial models or be exceedingly simplistic. In either case, the advent of low-voltage irons and active tips have made self-built soldering stations much more approachable. Attempts without the use of these modern niceties tended to be somewhat less glamorous.




![[Boltz999]'s carrot interconnect.](https://hackaday.com/wp-content/uploads/2019/12/carrot-interconnect.jpg?w=400)