I recently spent a largely sleepless night at a hotel, and out of equal parts curiosity and boredom, decided to kill some time scanning the guest network to see what my fellow travelers might be up to. As you’d probably expect, I saw a veritable sea of Samsung and Apple devices. But buried among the seemingly endless number of smartphones charging next to their sleeping owners, I found something rather interesting. I was as picking up a number of Amazon-made devices, all of which had port 5555 open.
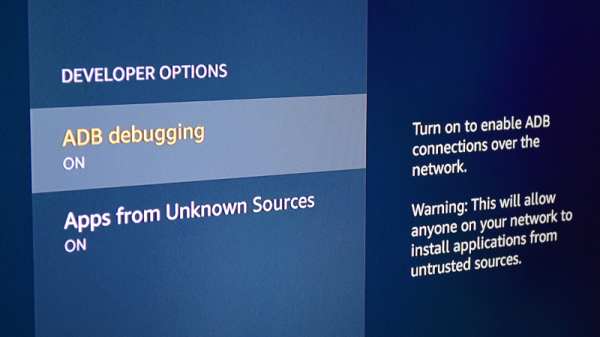
As a habitual Android tinkerer, this struck me as very odd. Port 5555 is used for Android Debug Bridge (ADB), a development tool used to control and perform various administrative tasks on an Android device over the network or (more commonly) locally over USB. The number of users who would have legitimately needed to enable network ADB on their devices is surely rather low, so to see a half dozen of them on the network at the same time seemed improbable to say the least.
Why would so many devices manufactured by Amazon all have network ADB enabled? I realized there must be a connection, and it didn’t take long to figure it out.