Most readers will be aware of the various distributed computing projects that provide supercomputer-level resources to researchers by farming out the computing tasks across a multitude of distributed CPUs and GPUs. The best known of these are probably Folding@Home and Rosetta, which have both this year been performing sterling service in the quest to understand the mechanisms of the SARS COVID-19 virus. So far these two platforms have remained available nearly exclusively for Intel-derived architectures, leaving the vast number of ARM-based devices out in the cold. It’s something the commercial distributed-computing-on-your-phone company Neocortix have addressed, as they have successfully produced ARM64 clients for both platforms that will be incorporated into the official clients in due course.
So it seems that mundane devices such as mobile phones and the more capable Raspberry Pi boards will now be able to fold proteins like a boss, and the overall efforts to deliver computational research will receive a welcome boost. But will there be any other benefits? It’s a Received Opinion that ARM chips are more power-efficient than their Intel-derived cousins, but will this deliver more energy-efficient distributed computing? The answer is “probably”, but the jury’s out on that one as computationally intensive tasks are said to erode the advantage significantly.
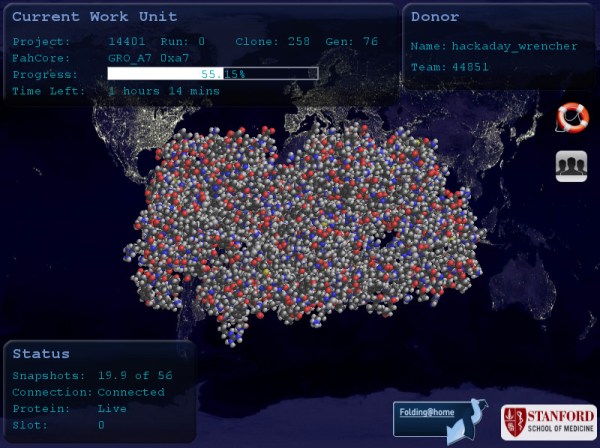
Folding@Home was catapulted by the influx of COVID-19 volunteers into first place as the world’s largest supercomputer earlier this year, and we’re pleased to say that Hackaday readers have played their part in that story. As this is being written the July 2020 stats show our team ranked at #39 worldwide, having racked up 14,005,664,882 points across 824,842 work units. Well done everybody, and we look forward to your ARM phones and other devices boosting that figure. If you haven’t done so yet, download the client and join us..
Via HPCwire. Thanks to our colleague [Sophi] for the tip.