So, maybe right now isn’t the best time to get into the high-altitude ballooning hobby? At least in the US, which with the downing of another — whatever? — over Alaska, seems to have taken a “Sidewinders first, threat identification later” approach to anything that floats by. The latest incident involved an aircraft of unknown type, described as “the size of a small car” — there’s that units problem again — that was operating over Prudhoe Bay off the northern coast of Alaska. The reason that was given for this one earning a Sidewinder was that it was operating much lower than the balloon from last week, only about 40,000 feet, which is well within the ceiling of commercial aviation. It was also over sea ice at the time of the shootdown, making the chance of bothering anyone besides a polar bear unlikely. We’re not taking any political position on this whole thing, but there certainly are engineering and technical aspects of these shootdowns that are pretty interesting, as well as the aforementioned potential for liability if your HAB goes astray. Nobody ever really benefits from having an international incident on their resume, after all.
Slider4929 Articles
Hackaday Podcast 205: Hackaday Berlin, So Many Sundials, And Ovens Pinging Google
Editor-in-Chief Elliot Williams and Managing Editor Tom Nardi start this week’s episode off with the announcement of Hackaday Berlin on March 25th. It’s been quite some time since we’ve been on the other side of the pond, because we had to cancel 2020’s Hackaday Belgrade due to COVID-19, so excitement is high for all three days of this “one-day” event.
After a new What’s that Sound, discussion moves on to an impressive collection of DIY sundials, the impact filament color has on the strength of 3D printed parts, the incredible retrocomputer replicas of Michael Gardi, and the Arduino FPGA that you’ve probably never heard of. We’ll wrap things up with the unexpected difficulties of mixing multiple cheap audio sources in Linux, and try to figure out why our kitchen appliances need to be connected to the Internet.
Check out the links below if you want to follow along, and as always, tell us what you think about this episode in the comments!
Continue reading “Hackaday Podcast 205: Hackaday Berlin, So Many Sundials, And Ovens Pinging Google”
This Week In Security: ImageMagick, VBulletin, And Dota 2
There are a few binaries that wind up running in a bunch of places, silently do their jobs, and being easily forgotten about. ImageMagick is used on many servers for image conversion and resizing, and tends to run automatically on uploaded images. Easily forgotten, runs automatically, and with arbitrary inputs. Yep, perfect target for vulnerability hunting. And the good folks at Metabase found two of them.
First up is CVE-2022-44267, a Denial of Service, when ImageMagick tries to process a rigged PNG that contains a textual chunk. This data type is usually used for metadata, and can include a profile entry for something like EXIF data. If this tag is specified inside a text chunk, ImageMagick looks to the given value as a filename for finding that profile data. And notably, if that value is a dash -, it tries to read from standard input. If the server’s image processing flow doesn’t account for that quirk, and virtually none of them likely do, this means the ImageMagick process hangs forever, waiting for the end of input. So while that’s not usually a critical problem, it could be used for a resource exhaustion attack.
But the real problem is CVE-2022-44268. It’s the same trick, but instead of using - to indicate standard input, the processed image refers to a file on the server filesystem. If the file exists, and can be read, the contents are included in the image output. If the attacker has access to the image, it’s a slick data leak — and obviously a real security problem. If a server doesn’t have tight file permissions and isolation, there’s plenty of sensitive information to be found and abused.
The fix landed back in October 2022, and was part of the 7.1.0-52 release. There’s a bit of uncertainty about which versions are vulnerable, but I wouldn’t trust anything older than that version. It’s a pretty straightforward flaw to understand and exploit, so there’s a decent chance somebody figured it out before now. The file exfiltration attack is the one to watch out for. It looks like there’s an Indicator of Compromise (IoC) for those output PNGs: “Raw profile type”. Continue reading “This Week In Security: ImageMagick, VBulletin, And Dota 2”
Ski Season Sees Apple’s Crash Detection System Fire Deluge Of False Positives
Smartphone features used to come thick and fast. Cameras proliferated, navigation got added, and then Apple changed the game by finally making touch computing just work. Since then, truly new features have slowed to a trickle, but Apple’s innovative crash detection system has been a big deal where safety is concerned.
The problem? It’s got a penchant for throwing false positives when iPhone and Apple Watch users are in no real danger at all. We first covered this problem last year, but since then, the wintery season has brought yet more issues for already-strained emergency responders.
Continue reading “Ski Season Sees Apple’s Crash Detection System Fire Deluge Of False Positives”
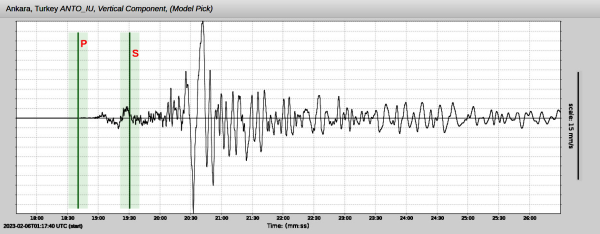
Ask Hackaday: Incidental Earthquake Detection
It never seems to fail: at the very moment that human society seems to reach a new pinnacle of pettiness, selfishness, violence, and self-absorption, Mother Nature comes along and reminds us all who’s really in charge. The obvious case in point here is the massive earthquakes near the border of Turkey and Syria, the appalling loss of life from which is only now becoming evident, and will certainly climb as survivors trapped since the Monday quakes start to succumb to cold and starvation.
Whatever power over nature we think we can wield pales by comparison with the energy released in this quake alone, which was something like 32 petajoules. How much destruction such a release causes depends on many factors, including the type of quake and its depth, plus the soil conditions at the epicenter. But whatever the local effects on the surface, quakes like these have a tendency to set the entire planet ringing like a bell, with seismic waves transmitted across the world that set the needles of professionally maintained seismometers wiggling.
For as valuable as these seismic networks are, though, there’s a looser, ad hoc network of detection instruments that are capable of picking up quakes as large as these from half a planet away. Some are specifically built to detect Earth changes, while some are instruments that only incidentally respond to the shockwaves traveling through the planet. And we want to know if this quake showed up in the data from anyone’s instruments.
Continue reading “Ask Hackaday: Incidental Earthquake Detection”
Linux Fu: The Shell Forth Programmers Will Love
One of the most powerful features of Unix and Linux is that using traditional command line tools, everything is a stream of bytes. Granted, modern software has blurred this a bit, but at the command line, everything is text with certain loose conventions about what separates fields and records. This lets you do things like take a directory listing, sort it, remove the duplicates, and compare it to another directory listing. But what if the shell understood more data types other than streams? You might argue it would make some things better and some things worse, but you don’t have to guess, you can install cosh, a shell that provides tools to produce and work with structured data types.
The system is written with Rust, so you will need Rust setup to compile it. For most distributions, that’s just a package install (rust-all in Ubuntu-like distros, for example). Once you have it running, you’ll have a few new things to learn compared to other shells you’ve used. Continue reading “Linux Fu: The Shell Forth Programmers Will Love”
Keebin’ With Kristina: The One With The Breadboard Macropad
 For their first custom, hand-wired keyboard, [terryorchard] aka [70rch] didn’t want to mess with making a total split, and we don’t really blame them. However, as you can see, they ended up with a monoblock split, which aside from being our own personal preference, looks fantastic, and also happened to be what fit on the print bed.
For their first custom, hand-wired keyboard, [terryorchard] aka [70rch] didn’t want to mess with making a total split, and we don’t really blame them. However, as you can see, they ended up with a monoblock split, which aside from being our own personal preference, looks fantastic, and also happened to be what fit on the print bed.
What you’re looking at is a 40% remix of the Alice layout with a columnar stagger. It’s also a bit 6×3 Corne-inspired on the ergonomic front. Brain-wise, it’s got an exposed Elite Pi driving a matrix of Kailh Choc pinks and an EC11 encoder. The encoder scrolls by default, and then becomes a volume knob on the numbers and symbols layer. One super cool thing about this keyboard is the secret third layer, which is unlocked by pressing the rotary encoder. This leads to some home row mods and disables the outside columns, culminating in a test 3×5 with two layers.
Via KBD #112
Continue reading “Keebin’ With Kristina: The One With The Breadboard Macropad”