One of the more exciting prospects upon receiving one of the earliest Raspberry Pi boards back in 2012 was that it was a fully-functional desktop computer in the palm of your hand. In those far-off days, the Debian OS distro for the board wasn’t even yet called Raspbian, but it would run a full-on desktop on your TV and you could use it after a fashion to browse the web or do wordprocessing. It wasn’t in any way fast, but it was usable enough to be more than a novelty. I’ve said before on these pages that the Raspberry Pi folks’ key product is their OS rather than their computers. While they rarely have the fastest or highest spec hardware, you can depend on Raspberry Pi OS being updated and supported through the life of the board unlike many of their competitors. I can download their latest OS image and still run it on that 2012 board, which to me ranks as a very laudable achievement.
The OS They Don’t Really Tell You About
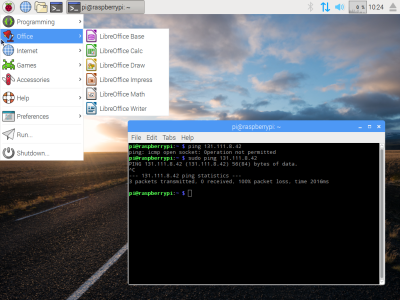
Raspberry Pi OS doesn’t run on any other ARM single board computers but their own, but it’s not quite accurate to say that it only runs on Raspberry Pi hardware. Since 2016 when it was launched as PIXEL, the folks in Cambridge have also maintained a PC version for 32-bit i386 computers, now called Raspberry Pi Desktop. It may be the Pi product they don’t talk about much, but you can still find it on their downloads page.
Like the ARM version, it’s based on Debian and presents as close as possible to the environment you’d find on your Pi. I’m interested to see whether it still lives up to the claim of being usable on older hardware, so I’ve downloaded a copy and installed it on my trusty 2007 Dell Inspiron 640. It rocks a 1.6 GHz Core Duo with 4 GB of memory and a SATA SSD so it’s not the lowest spec hardware on the block, but by 2023’s standard it represents a giveaway-spec old laptop. Can I use it as a daily driver? Let’s find out! Continue reading “Jenny’s Daily Drivers: Raspberry Pi Desktop”