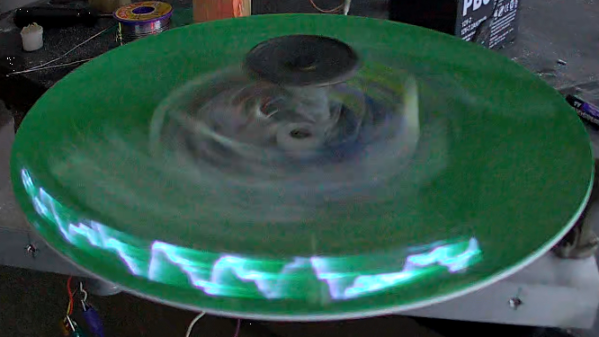
A question for you: if the cathode ray tube had never been invented, what would an oscilloscope look like? We’re not sure ourselves, but it seems like something similar to this mechanical tachyscope display might worked, at least up to a point.
What’s ironic about this scenario is that the tachyscope [Daniel Ross] built actually uses a CRT from a defunct camcorder viewfinder as the light-up bit of what amounts to a large POV display. The CRT’s horizontal coil is disconnected while the vertical coil is attached to the output of a TEA205B audio amplifier. The CRT, its drive electronics, and the amp are mounted to a motorized plastic platter along with a wireless baby monitor, to send audio to the CRT without the need for slip rings — although a Bluetooth module appears to be used for that job in the video below.
Speaking of slip rings, you’d expect one to make an appearance here to transfer power to the platter. [Daniel] used a slip ring for his previous steampunk tachyscope, but this time out he chose a hand-wound air core transformer, with a stationary primary coil and secondary coil mounted on the platter. With a MOSFET exciter on the primary and a bridge rectifier on the secondary, he’s able to get the 12 volts needed to power everything on the platform.
Like most POV displays, this one probably looks better in person than it does in video. But it’s still pretty cool, with the audio waveforms sort of floating in midair as the CRT whizzes around. [Daniel] obviously put a lot of work into this, not least with the balancing necessary to get this running smoothly, so hats off for the effort.
Continue reading “Spinning CRT Makes A 360 Degree Audio Oscilloscope”