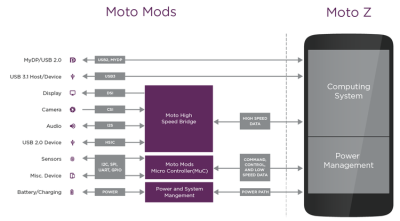
In the surest sign that hardware hacking is the new hotness, Motorola and Farnell/Element 14 have developed an add-on board and SDK that will let you connect virtually anything to your mobile phone. Motorola is calling it the “Moto Mods” system, and it looks like its going to be a dedicated microcontroller that interfaces with the computer inside the phone and provides everything from GPIOs to DSI (video). Naturally, I2C, I2S, SPI, UART, even two flavors of USB are in the mix.
The official SDK, ahem Mods Development Kit (MDK), is based on the open Greybus protocol stack (part of Google’s Project Ara open phone project) and it’s running on an ARM Cortex-M4F chip. It’s likely to be itself fairly hackable, and even if the suggested US $125 price is probably worth it for the convenience, we suspect that it’ll be replicable with just a few dollars in parts and the right firmware. (Yes, that’s a challenge.)
The initial four adapter boards range from a simple breadboard to a Raspberry-Pi-hat adapter (hence the title). It’s no secret that cell phones now rival the supercomputers of a bygone era, but they’ve always lacked peripheral interfaces. We wish that all of the old smartphones in our junk box had similar capabilities. What do you say? What would you build with a cellphone if you could break out all sorts of useful comms?
Via HackerBoards, and thanks to [Tom] for the tip!