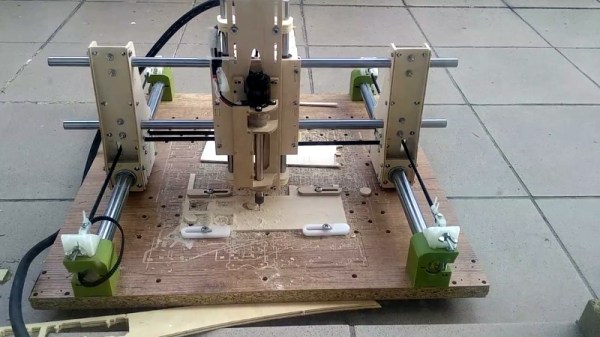
If you’re building a CNC router, laser cutter, or even 3D printer, you’ll usually be looking at a dedicated controller. This board takes commands from a computer, often in the form of G-Code, and interprets that into movement commands to the connected stepper motors. Historically this has been something of a necessary evil, as there was really no way to directly control stepper motors with a computer fast enough to be useful. That may not be the case anymore.

Thanks to the Raspberry Pi (and similar boards), we now have Linux computers with plenty of GPIO pins. The only thing missing is the software to interpret the G-Code and command the steppers over GPIO, which thanks to [pantadeusz], we now have. Called raspigcd, this software interprets a subset of G-Code to provide real-time control over connected steppers fast enough to drive a small CNC router.
Of course, you can’t directly control a beefy stepper motor to the GPIO pins of a Pi. You’ll let out all the magic smoke. But you can wire it up directly to a stepper driver board. These little modules connect up to a dedicated power supply and handle the considerable current draw of the steppers, all you need to do is provide them the number of steps and direction of travel.
This method of direct control offers some very interesting possibilities for small, low-cost, CNC projects. Not only can you skip the control board, you could conceivably handle the machine’s user interface (either directly via a touch screen or over the network) on the same Pi.
We’ve seen attempts at creating all-in-one Linux stepper controllers in the past, but the fact that anyone with a Raspberry Pi 2 or 3 (the boards this software has currently been tested on) can get in on the action should really help spur along development. Has anyone used this?