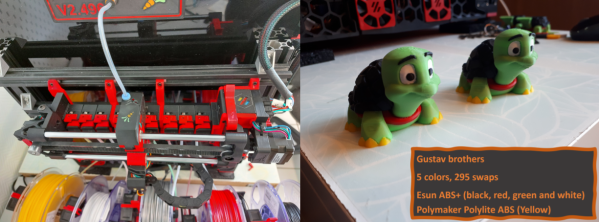
Multimaterial printing was not invented by BambuLabs, but love them or hate them the AMS has become the gold standard for a modern multi-material unit. [Daniel]’s latest Mod Bot video on the Box Turtle MMU (embedded below) highlights an open source project that aims to bring the power and ease of AMS to Voron printers, and everyone else using Klipper willing to put in the work.

The system itself is a mostly 3D printed unit that sits atop [Daniel]’s Voron printer looking just like an AMS atop a BambuLab. It has space for four spools, with motorized rollers and feeders in the front that have handy-dandy indicator LEDs to tell you which filament is loaded or printing. Each spool gets its own extruder, whose tension can be adjusted manually via thumbscrew. A buffer unit sits between the spool box and your toolhead.
Aside from the box, you need to spec a toolhead that meets requirements. It needs a PTFE connector with a (reverse) boden tube to guide the filament, and it also needs to have a toolhead filament runout sensor. The sensor is to provide feedback to Klipper that the filament is loaded or unloaded. Finally you will probably want to add a filament cutter, because that happens at the toolhead with this unit. Sure, you could try the whole tip-forming thing, but anyone who had a Prusa MMU back in the day can tell you that is easier said than done. The cutter apparently makes this system much more reliable.
Continue reading “Is Box Turtle The Open Source AMS We’ve Been Waiting For?”








 Are all cheap multimeter leads similarly useless? Not necessarily. [nop head] also purchased the set pictured here. It has no attachments, but was a much better design and had a resistance of only 64 milliohms. Not great, but certainly serviceable and clearly a much better value than the other set.
Are all cheap multimeter leads similarly useless? Not necessarily. [nop head] also purchased the set pictured here. It has no attachments, but was a much better design and had a resistance of only 64 milliohms. Not great, but certainly serviceable and clearly a much better value than the other set.