A friend of ours once described computers as “high-speed idiots.” It was true in the 80s, and it appears that even with the recent explosion in AI, all computers have managed to do is become faster. Proof of that can be found in a story about using ASCII art to trick a chatbot into giving away the store. As anyone who has played with ChatGPT or its moral equivalent for more than five minutes has learned, there are certain boundary conditions that the LLM’s creators lawyers have put in place to prevent discussion surrounding sensitive topics. Ask a chatbot to deliver specific instructions on building a nuclear bomb, for instance, and you’ll be rebuffed. Same with asking for help counterfeiting currency, and wisely so. But, by minimally obfuscating your question by rendering the word “COUNTERFEIT” in ASCII art and asking the chatbot to first decode the word, you can slip the verboten word into a how-to question and get pretty explicit instructions. Yes, you have to give painfully detailed instructions on parsing the ASCII art characters, but that’s a small price to pay for forbidden knowledge that you could easily find out yourself by other means.
Slider4929 Articles
Hackaday Podcast Episode 262: Wheelchair Hacking, Big Little Science At Home, Arya Talks PCBs
Join Hackaday Editors Elliot Williams and Tom Nardi as they go over their favorite hacks and stories from the past week. This episode starts off with an update on Hackaday Europe 2024, which is now less than a month away, and from there dives into wheelchairs with subscription plans, using classic woodworking techniques to improve your 3D printer’s slicer, and a compendium of building systems. You’ll hear about tools for finding patterns in hex dumps, a lusciously documented gadget for sniffing utility meters, a rare connector that works with both HDMI and DisplayPort, and a low-stress shortwave radio kit with an eye-watering price tag. Finally, they’ll take a close look at a pair of articles that promise to up your KiCAD game.
Check out the links below if you want to follow along, and as always, tell us what you think about this episode in the comments!
This Week In Security: Apple Backdoors Curl, Tor’s New Bridge, And GhostRace
OK, that headline is a bit of a cheap shot. But if you run the curl binary that Apple ships, you’re in for a surprise if you happen to use the --cacert flag. That flag specifies that TLS verification is only to be done using the certificate file specified. That’s useful to solve certificate mysteries, or to make absolutely sure that you’re connecting to the server you expect.
What’s weird here is that on a MacOS, using the Apple provided curl binary, --cacert doesn’t limit the program to the single certificate file. On an Apple system, the verification falls back to the system’s certificate store. This is an intentional choice by Apple, but not one that’s aimed particularly at curl. The real magic is in Apple’s SSL library, which forces the use of the system keychain.
The current state of things is that this option is simply not going to do the right thing in the Apple provided binary. It’s documented with the note that “this option is supported for backward compatibility with other SSL engines, but it should not be set.” It’s an unfortunate situation, and we’re hopeful that a workaround can be found to restore the documented function of this option. Continue reading “This Week In Security: Apple Backdoors Curl, Tor’s New Bridge, And GhostRace”
Retrotechtacular: Air Mail For The Birds
Today, if you want to send a message to a distant location, you’ll probably send an e-mail or a text message. But it hasn’t always been that easy. Military commanders, in particular, have always needed ways to send messages and were early adopters of radio and, prior to that, schemes like semaphores, drums, horns, Aldis lamps, and even barrels of water to communicate over distances.
One of the most reliable ways to pass messages, even during the last world war, was by carrier pigeon. Since the U.S. Army Signal Corps handled anything that included messages, it makes sense that the War Department issued TM 11-410 about how to use and care for pigeons. Think of it as the network operations guide of 1945. The practice, though, is much older. There is evidence that the Persians used pigeons in the 6th century BC, and Julius Caesar’s army also used the system.
You wouldn’t imagine that drawing an assignment in the Signal Corps might involve learning about breeding pigeons, training them, and providing them with medical attention, but that’s what some Signal Corps personnel did. The Army started experimenting with pigeons in 1878, but the Navy was the main user of the birds until World War I, when the U.S. Pigeon Intelligence Service was formed. In World War II, they saw use in situations where radio silence was important, like the D-Day invasion.
The Navy also disbanded its earlier Pigeon Messenger Service. It then returned to avian communications during the World Wars, using them to allow aviators to send messages back to base without radio traffic. The Navy had its own version of the pigeon manual.
Lithium-Ion Batteries Power Your Devboards Easily
Last summer, I was hanging out with a friend from Netherlands for a week, and in the middle of that week, we decided to go on a 20 km bike trip to a nearby beach. Problem? We wanted to chat throughout the trip, but the wind noise was loud, and screaming at each other while cycling wouldn’t have been fun. I had some walkie-talkie software in mind, but only a single battery-powered Pi in my possession. So, I went into my workshop room, and half an hour later, walked out with a Pi Zero wrapped in a few cables.
I wish I could tell you that it worked out wonders. The Zero didn’t have enough CPU power, I only had single-core ones spare, and the software I had in mind would start to badly stutter every time we tried to run it in bidirectional mode. But the battery power solution was fantastic. If you need your hack to go mobile, read on.
Continue reading “Lithium-Ion Batteries Power Your Devboards Easily”
Review: The New Essential Guide To Electronics In Shenzhen
The city of Shenzhen in China holds a special fascination for the electronic hardware community, as the city and special economic zone established by the Chinese government at the start of the 1980s it has become probably one of the most important in the world for electronic manufacturing. If you’re in the business of producing electronic hardware you probably want to do that business there, and if you aren’t, you will certainly own things whose parts were made there. From the lowly hobbyist who buys a kit of parts on AliExpress through the project featured on Hackaday with a Shenzhen-made PCB, to the engineer bringing an electronic product to market, it’s a place which has whether we know it or not become part of our lives.
First, A Bit Of History

At a superficial level it’s very easy to do business there, as a quick trawl through our favourite Chinese online retailers will show. But when you’ve graduated from buying stuff online and need to get down to the brass tacks of sourcing parts and arranging manufacture, it becomes impossible to do so without being on the ground. At which point for an American or European without a word of Chinese even sourcing a resistor becomes an impossibly daunting task. To tackle this, back in 2016 the Chinese-American hardware hacker and author Andrew ‘bunnie’ Huang produced a slim wire-bound volume, The Essential Guide to Electronics in Shenzhen. This book contained both a guide to the city’s legendary Huaquanbei electronics marts and a large section of point-to-translate guides for parts, values, and all the other Chinese phrases which a non-Chinese-speaker might need to get their work done in the city. It quickly became an essential tool for sourcing in Shenzhen, and more than one reader no doubt has a well-thumbed copy on their shelves.
There are places in the world where time appears to move very slowly, but this Chinese city is not one of them. A book on Shenzhen written in 2016 is now significantly out of date, and to keep pace with its parts that have since chanced beyond recognition, an update has become necessary. In this endeavour the mantle has passed to the hardware hacker and Shenzhen native Naomi Wu, someone with many years experience in introducing the people, culture, and industries of her city to the world. Her updated volume, The New Essential Guide to Electronics in Shenzhen has been the subject of a recent crowdfunding effort, and I was lucky enough to snag one. It’s a smart hardcover spiral-bound book with a red and gold cover, and it’s time to open it up and take a look. Continue reading “Review: The New Essential Guide To Electronics In Shenzhen”
The Short Workbench
Imagine an electronics lab. If you grew up in the age of tubes, you might envision a room full of heavy large equipment. Even if you grew up in the latter part of the last century, your idea might be a fairly large workbench with giant boxes full of blinking lights. These days, you can do everything in one little box connected to a PC. Somehow, though, it doesn’t quite feel right. Besides, you might be using your computer for something else.
I’m fortunate in that I have a good-sized workspace in a separate building. My main bench has an oscilloscope, several power supplies, a function generator, a bench meter, and at least two counters. But I also have an office in the house, and sometimes I just want to do something there, but I don’t have a lot of space. I finally found a very workable solution that fits on a credenza and takes just around 14 inches of linear space.
How?
How can I pack the whole thing in 14 inches? The trick is to use only two boxes, but they need to be devices that can do a lot. The latest generation of oscilloscopes are quite small. My scope of choice is a Rigol DHO900, although there are other similar-sized scopes out there.
If you’ve only seen these in pictures, it is hard to realize how much smaller they are than the usual scopes. They should put a banana in the pictures for scale. The scope is about 10.5″ wide (265 mm and change). It is also razor thin: 3″ or 77 mm. For comparison, that’s about an inch and a half narrower and nearly half the width of a DS1052E, which has a smaller screen and only two channels.
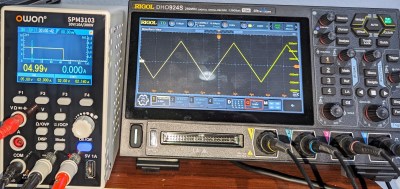
If you get the scope tricked out, you’ve just crammed a bunch of features into that small space. Of course, you have a scope and a spectrum analyzer. You can use the thing as a voltmeter, but it isn’t the primary meter on the bench. If you spend a few extra dollars, you can also get a function generator and logic analyzer built-in. Tip: the scope doesn’t come with the logic analyzer probes, and they are pricey. However, you can find clones of them in the usual places that are very inexpensive and work fine.
There are plenty of reviews of this and similar scopes around, so I won’t talk anymore about it. The biggest problem is where to park all the probes. Continue reading “The Short Workbench”