It wasn’t long ago that we introduced you to a web site, the Godbolt compiler explorer, that allows the visitor to compile code using a slew of compilers and compare their output. We suspect some number of readers said, “Wow! I can use that!”, while perhaps everyone else said, “Huh?” Well if you were in the second group, you ought to watch [What’s a Creel’s] video below where he walks through using the website. He looks at four different algorithms using four different compilers and it is a good example of how you might use the tool to make decisions about how you write software.
Software Hacks1035 Articles
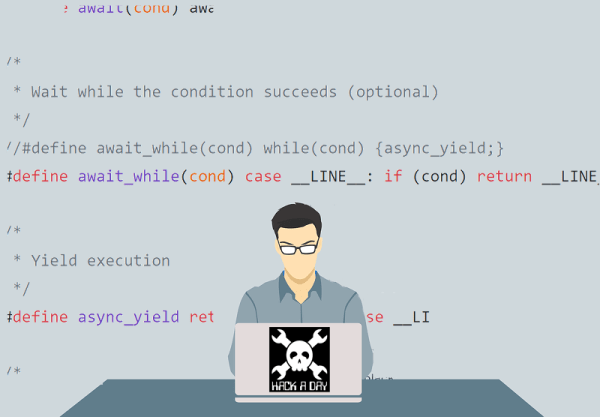
Asynchronous Routines For C
[Sandro Magi] noted that the async/await idiom has become more prevalent in programming recently. According to him, he first encountered it in C# but has found examples of it in JavaScript and Rust, too. The idea is simple: allow a function to return but come back later to complete something that takes a long time. Of course, multithreading is one answer to this, but generally, this technique implies more of a coroutine setup where functions cooperate to some degree to get good behavior. [Sandro] took some ideas from the existing protothread library and used it to create a system to get this effect in C and, by extension, C++.
Adding this “library” is as simple as including a header file. All the magic occurs at the preprocessor and compiler. There’s no code to link. The async routines only need two bytes of overhead and — unlike proper threads — don’t need a preallocated private stack.
Control Lighting Effects Without Programming
Working in a theater or night club often requires a specialized set of technical skills that you might not instantly think about. Sure, the audio system needs to be set up and managed but the lighting system is often actively managed as well. For simple setups, this is usually not too difficult to learn. With more complicated systems you will need to get elbow-deep into some software. With [trackme518]’s latest tool, though, you will only need to be able to edit video.
Sure, this sounds like just trading one piece of software for another, but it’s more likely that professionals working in lighting will already know how to edit video rather than know programming or complicated proprietary lighting software. All you have to do to control a set of lights is to create a video, or use an existing one, and the lighting system will mimic the video on its own. If you do know programming, though, it’s written in Processing Java so changes aren’t too difficult to make.
The software (available on the project’s GitHub page) will also work outside of a professional environment, as well. It’s set up to work with DMX systems as well as LED strips so you could use it to run a large LED display board using only an input video as control. You could even use it to run the display on your guitar.
Photo courtesy of Rob Sinclair (Gribiche) [CC BY-SA 2.0 (https://creativecommons.org/licenses/by-sa/2.0)]
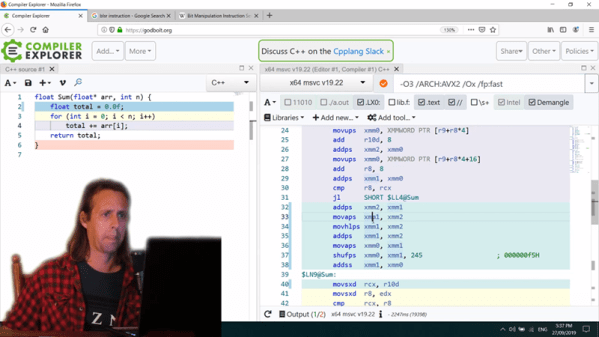
Peek Into The Compiler’s Code — Lots Of Compilers
We don’t know what normal people argue about, but we know we spend a lot of time arguing about the best microcontroller, which editor is the best, and what language or compiler does the best job. The problem with all those compilers is getting them loaded and digging into the generated code. If you too spend your time thinking about those things, you ought to have a look at [Matt Godbolt’s] Compiler Explorer. We know that hosting an IDE-like web page and compiling code is old hat — although [Matt’s] site has been around quite some time. But [Matt’s] doing it differently. The code you build on the left hand pane shows up as assembly language on the right hand side.
There are plenty of options, too. For example, here’s a bit of C code from the site’s example:
int square(int num) {
return num * num;
}
Here’s the corresponding assembly from gcc 9.2 for x86-64:
square: push rbp mov rbp, rsp mov DWORD PTR [rbp-4], edi mov eax, DWORD PTR [rbp-4] imul eax, eax pop rbp ret
Continue reading “Peek Into The Compiler’s Code — Lots Of Compilers”
This Week In Security: Simjacker, Microsoft Updates, Apple Vs Google, Audio DeepFakes, And NetCAT
We often think of SIM cards as simple data storage devices, but in reality a SIM card is a miniature Universal integrated circuit card, or smart card. Subscriber data isn’t a simple text string, but a program running on the smart cards tiny processor, acting as a hardware cryptographic token. The presence of this tiny processor in everyone’s cell phone was eventually put to use in the form of the Sim application ToolKit (STK), which allowed cell phone networks to add services to very basic cell phones, such as mobile banking and account management.
Legacy software running in a place most of us have forgotten about? Sounds like it’s ripe for exploitation. The researchers at Adaptive Mobile Security discovered that exploitation of SMS messages has been happening for quite some time. In an era of complicated and sophisticated attacks, Simjacker seems almost refreshingly simple. An execution environment included on many sim cards, the S@T Browser, can request data from the cell phone’s OS, and even send SMS messages. The attacker simply sends an SMS to this environment containing instructions to request the phones unique identifier and current GPS location, and send that information back in another SMS message.
It’s questionable whether there is actually an exploit here, as it seems the S@T Browser is just insecure by design. Either way, the fact that essentially anyone can track a cell phone simply by sending a special SMS message to that phone is quite a severe problem. Continue reading “This Week In Security: Simjacker, Microsoft Updates, Apple Vs Google, Audio DeepFakes, And NetCAT”
Lambdas For C — Sort Of
A lot of programming languages these days feature lambda functions, or what I would be just as happy to call anonymous functions. Some people make a big deal out of these but the core idea is very simple. Sometimes you need a little snippet of code that you only need in one place — most commonly, as a callback function to pass another function — so why bother giving it a name? Depending on the language, there can be more to it that, especially if you get into closures and currying.
For example, in Python, the map function takes a function as an argument. Suppose you have a list and you want to capitalize each word in the list. A Python string has a capitalize method and you could write a loop to apply it to each element in the list. However, map and a lambda can do it more concisely:
map(lambda x: x.capitalize(), ['madam','im','adam'])
The anonymous function here takes an argument x and calls the capitalize method on it. The map call ensures that the anonymous function is called once for each item.
Modern C++ has lambda expressions. However, in C you have to define a function by name and pass a pointer — not a huge problem, but it can get messy if you have a lot of callback functions that you use only one time. It’s just hard to think up that many disposable function names. However, if you use gcc, there are some nonstandard C features you can use to get most of what you want out of lambda expressions.
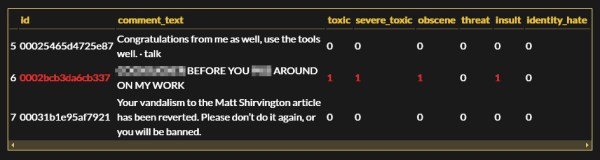
This Machine Learning Algorithm Is Meta
Suppose you ran a website releasing many articles per day about various topics, all following a general theme. And suppose that your website allowed for a comments section for discussion on those topics. Unless you are brand new to the Internet, you’ll also imagine that the comments section needs at least a little bit of moderation to filter out spam, off topic, or even toxic comments. If you don’t want to employ any people for this task, you could try this machine learning algorithm instead.
[Ladvien] goes through a general overview of how to set up a convolutional neural network (CNN) which can be programmed to do many things, but this one crawls a web page, gathers data, and also makes decisions regarding that data. In this case, the task is to identify toxic comments but the goal is not to achieve the sharpest sword in the comment moderator’s armory, but to learn more about how CNNs work.
Written in Python, the process outlines the code itself and how it behaves, setting up a small server to host the neural network, and finally creating the webservice. As with any machine learning, you need a reliable dataset to use for training and this one came from Wikipedia comments previously flagged by humans. Trolling nuance is thrown aside, as the example homes in on blatant insults and vulgarity.
While [Ladvien] notes that his guide isn’t meant to be comprehensive, but rather to fill in some gaps that he noticed within other guides like this, we find this to be an interesting read. He also mentioned that, in theory, this tool could be used to predict the number of comments following an article like this very one based on the language in the article. We’ll leave that one as an academic exercise for now, probably.