There is a gotcha lurking in wait for hackers who look at a piece of equipment, see a port labeled “Serial / RS-232”, and start to get ideas. The issue is the fact that the older the equipment, the more likely it is to be a bit old-fashioned about how it expects to speak RS-232. Vintage electronics may expect the serial data to be at bipolar voltage levels that are higher than what the typical microcontroller is used to slinging, and that was the situation [g3gg0] faced with some vintage benchtop equipment. Rather than deal with cables and wired adapters, [g3gg0] decided to design a wireless adapter with WiFi and Bluetooth on one end, and true RS-232 on the other.
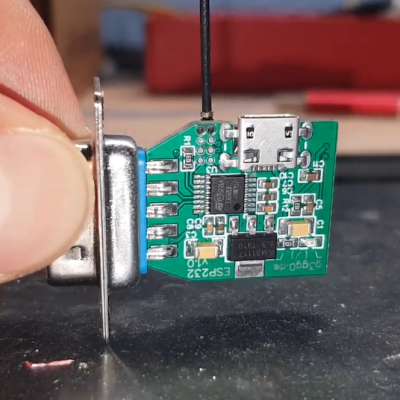 The adapter features an ESP32 and is attached to a DB-9 plug, so it’s nice and small. It uses the ST3232 chip to communicate at 3 V logic levels on the microcontroller side, supports bipolar logic up to +/-13 V on the vintage hardware side, and a rudimentary web interface allows setting hardware parameters like baud rate. The nice thing about the ST3232 transceiver is that it is not only small, but can work from a 3 V supply with only four 0.1 uF capacitors needed for the internal charge pumps.
The adapter features an ESP32 and is attached to a DB-9 plug, so it’s nice and small. It uses the ST3232 chip to communicate at 3 V logic levels on the microcontroller side, supports bipolar logic up to +/-13 V on the vintage hardware side, and a rudimentary web interface allows setting hardware parameters like baud rate. The nice thing about the ST3232 transceiver is that it is not only small, but can work from a 3 V supply with only four 0.1 uF capacitors needed for the internal charge pumps.
As for actually using the adapter, [g3gg0] says that the adapter’s serial port is exposed over TCP on port 23 (Telnet) which is supported by some programs and hardware. Alternately, one can connect an ESP32 to one’s computer over USB, and run firmware that bridges any serial data directly to the adapter on the other end.
Design files including schematic, bill of materials, and PCB design are shared online, and you can see a brief tour of the adapter in the video, embedded below.
Continue reading “DIY Wireless Serial Adapter Speaks (True) RS-232”