You have to be pretty ambitious to modify a clock to run for 50 years on a single battery. You also should probably be pretty young if you think you’re going to verify your power estimates, at least in person. According to [Josh EJ], this modified quartz analog clock, which ticks off the date rather than the time, is one of those “The March of Time” projects that’s intended to terrify incentivize you by showing how much of the year is left.
Making a regular clock movement slow down so that what normally takes an hour takes a month without making any mechanical changes requires some clever hacks. [Josh] decided to use an Arduino to send digital pulses to the quartz movement to advance the minute hand, rather than let it run free. Two pulses a day would be perfect for making a 30-day month fit into a 60-minute hour, but that only works for four months out of the year. [Josh]’s solution was to mark the first 28 even-numbered minutes, cram 29, 30, and 31 into the last four minutes of the hour, and sort the details out in code.
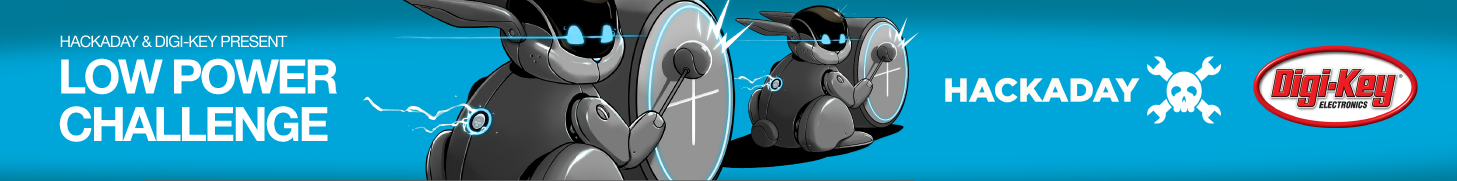
As for the low-power mods, there’s some cool wizardry involved with that, like flashing the Arduino Pro Mini with a new bootloader that reduces the clock speed to 1 MHz. This allows the microcontroller and RTC module to run from the clock movement’s 1.5 V AA battery. [Josh] estimates a current draw of about 6 μA per day, which works out to about 50 years from a single cell. That’s to be taken with a huge grain of salt, of course, but we expect the battery will last a long, long time.
[Josh] built this clock as part of the Low-Power Challenge contest, which wrapped up this week. We’re looking forward to the results of the contest — good luck to all the entrants!