For anyone serious about mining cryptocurrency such as Bitcoin, we’re well past the point where a standard desktop computer is of much use. While an array of high-end GPUs is still viable for some currencies, the real heavy hitters are using custom mining hardware that makes use of application-specific integrated circuits (ASICs) to crunch the numbers. But eventually even the most powerful mining farm will start to show its age, and many end up selling on the second hand market for pennies on the dollar.
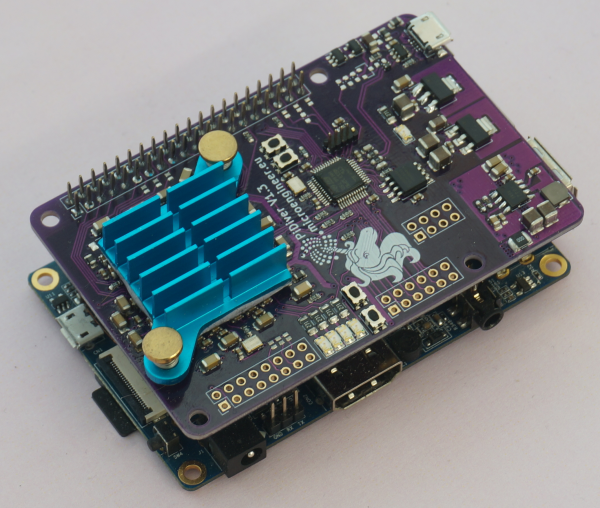
Naturally, hackers are hard at work trying to find alternate uses for these computational powerhouses. While it won’t teach an old ASIC a new trick, [xjtuecho] has documented some very interesting details on the FPGA control board of the Ebit E9+ Bitcoin miner. Known as the EBAZ4205, this board can be purchased for around $20 USD from online importers and even less if you can find one used. Since it’s just the controller it won’t help you build a budget super computer, but there’s always interest in cheap FPGA development boards.

According to [xjtuecho], it takes a little bit of work to get the EBAZ4205 ready for experimentation. For one thing, you may have to solder on your own micro SD slot depending on where you got the board from. You’ll also need to add a couple diodes to configure which storage device to boot from and to select where the board pulls power from.
Once you’re done, you’ll have a dual core Cortex A9 Linux board with 256 MB DDR3 and a Artix-7 FPGA featuring 28K logic elements to play with. Where you go from there is up to you.
This isn’t the first time we’ve seen FPGA boards hit the surplus market at rock bottom prices. When IT departments started dumping their stock of Pano Logic thin clients back in 2013, a whole community of dedicated FPGA hackers sprouted up around it. We’re not sure the if the EBAZ4205 will enjoy the same kind of popularity in its second life, but the price is certainly right.
[Thanks to Rog77 for the tip.]