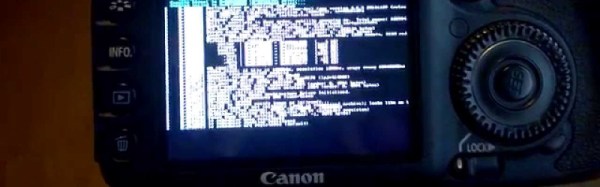
On April 1st the Magic Lantern team announced a proof of concept that lets you run Linux on a Canon EOS camera. Because of the date of the post we’ve poured over this one and are confident it’s no joke. The development has huge potential.
The hack was facilitated by a recent discovery that the LCD screen on the camera can be accessed from the bootloader. In case you don’t recognize the name, Magic Lantern is an Open Source project that adds features to these high-end cameras by utilizing the bootloader with binary files on the SD card. It’s long been a way of hacking more features in but has always been complicated by the fact that you must figure out how to play nicely with the existing firmware. Commanding the LCD was the last part of the hardware that had previously not been driven directly from Magic Lantern.
Now that the Linux kernel is in the picture, ground-up features can be built without dealing with the stock firmware in any way (and without overwriting it). We’re excited to see where this one goes. Currently it’s just a proof that you can boot Linux, it’s not actually functional yet. Here’s your chance to polish those kernel porting skills you’ve been holding in reserve.

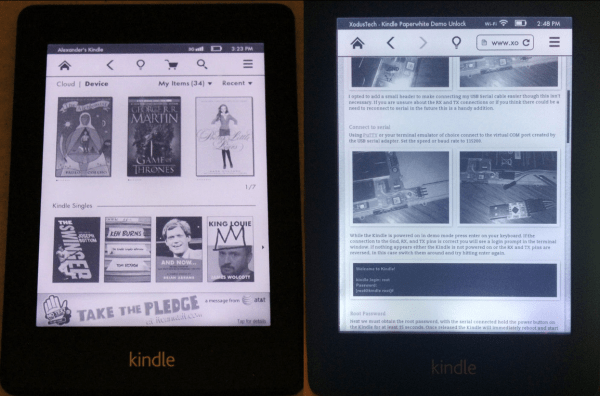
 The first step was to crack open the case and locate the serial port. [WarriorRocker] soldered a small three pin header to the pads to make it easier to work on his device as needed. He then connected the Kindle to his PC using a small serial to USB adapter. Pulling up the command prompt was as simple as running Putty and connecting to the correct COM port. If the wires are hooked up correctly, then it just takes a press of the enter key to pull up the login prompt.
The first step was to crack open the case and locate the serial port. [WarriorRocker] soldered a small three pin header to the pads to make it easier to work on his device as needed. He then connected the Kindle to his PC using a small serial to USB adapter. Pulling up the command prompt was as simple as running Putty and connecting to the correct COM port. If the wires are hooked up correctly, then it just takes a press of the enter key to pull up the login prompt.