OK, so maybe [satanistik] is overreaching with his project title “Save the Coffee, Save the World” but keeping an otherwise working coffee machine out of the landfill by hacking around its broken display is nonetheless a worthy pursuit. The juice must flow!
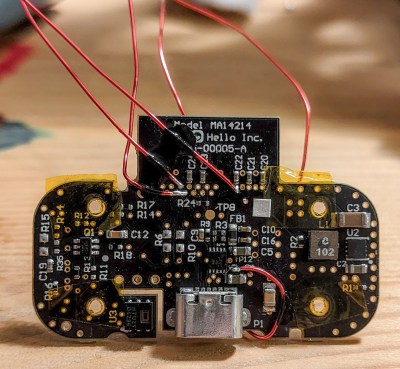
The busted display used a SSD1303 controller OLED module, for which the SSD1305Z is an almost-compatible module. Almost. The one glitch is that the screen is filled in the opposite direction by default. Digging through the manuals, there is a screen-direction bit to set, and tracing out the communication with a logic analyzer, it’s set the wrong way with every screen refresh. If only he could flip that one bit while it’s in transit. Time to man-in-the-middle!
While we certainly would have put a microcontroller in the game, [satanistik] goes old-school. A two-IC logic solution can do exactly the same thing, trading wires for code. The final iteration of the converter board is correspondingly spartan, but it does its one job.
So if you’ve got a Nivona coffee machine with a bum display, or perhaps an Agilent U1273A multimeter, or any other piece of equipment that needs a hard-to-find SSD1303 controller, now you have a ready-made solution. But if not, and you find yourself looking for a display that you can’t find, let this serve as an example to you – with a little (fun) effort, you can hack it back.