It can be jarring to see various sensors, smart switches, cameras, and other technology in a house built in the 1930s, like [Chris]’s was. But he still wanted presence detection so as to not stub any toes in the dark. The result is a sensor that blends in with the home’s aesthetics a bit better than anything you’re likely to find at the Big Box electronics store.
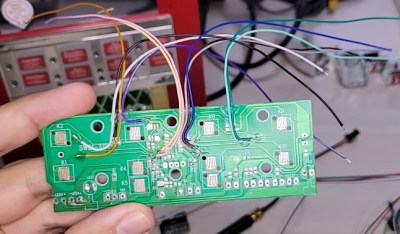
For the presence detection sensors, [Chris] chose to go with 24 GHz mmwave radar modules that, unlike infrared sensors, can detect if a human is in an area even if they are incredibly still. Paired with the diminutive ESP32-S2 Mini, each pair takes up very little real estate on a wall.
 Although he doesn’t have a 3D printer to really pare down the size of the enclosure to the maximum, he found pre-made enclosures instead that are fairly inconspicuous on the wall. Another design goal here was to make sure that everything was powered so he wouldn’t have to perpetually change batteries, so a small wire leads from the prototype unit as well.
Although he doesn’t have a 3D printer to really pare down the size of the enclosure to the maximum, he found pre-made enclosures instead that are fairly inconspicuous on the wall. Another design goal here was to make sure that everything was powered so he wouldn’t have to perpetually change batteries, so a small wire leads from the prototype unit as well.
The radar module and ESP pair are set up with some code to get them running in Home Assistant, which [Chris] has provided on the project’s page. With everything up and running he has a module that can control lights without completely changing the aesthetic or behavior of his home. If you’re still using other presence sensors and are new to millimeter wave radar, take a look at this project for a good guide on getting started with this fairly new technology.