Your first school. Your mother’s maiden name. Your favorite color. These are the questions we’re so used to answering when we’ve forgotten a password and need to get back into an account. They’re not a password, yet in many cases have just as much power. Despite this, they’re often based on incredibly insecure information.
Sarah Palin’s Yahoo account is perhaps the best example of this. In September 2008, a Google search netted a birthdate, ZIP code, and where the politician met her spouse. This was enough to reset the account’s password and gain full access to the emails inside.
While we’re not all public figures with our life stories splashed across news articles online, these sort of questions aren’t exactly difficult to answer. Birthdays are celebrated across social media, and the average online quiz would net plenty of other answers. The problem is that these questions offer the same control over an account that a password does, but the answers are not guarded in the same way a password is.
For this reason, I have always used complete gibberish when filling in security questions. Whenever I did forget a password, I was generally lucky enough to solve the problem through a recovery e-mail. Recently, however, my good luck ran out. It was a Thursday evening, and I logged on to check my forex trading account. I realised I hadn’t updated my phone number, which had recently changed.
Upon clicking my way into the account settings, I quickly found that this detail could only be changed by a phone call. I grabbed my phone and dialed, answering the usual name and date of birth questions. I was all set to complete this simple administrative task! I was so excited.
“Thanks Lewin, I’ll just need you to answer your security question.”
“Oh no.”
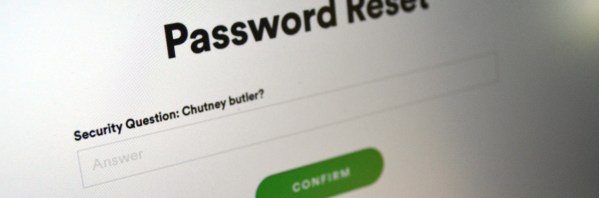
“The question is… Chutney butler?”
“Yes. Yes it is. Uh…”
“…would you like to guess?”
Needless to say, I didn’t get it.
I was beginning to sweat at this point. To their credit, the call center staffer was particularly helpful, highlighting a number of ways to recover access to the account. Mostly involving a stack of identification documents and a visit to the nearest office. If anything, it was a little reassuring that my account details required such effort to change. Perhaps the cellular carriers of the world could learn a thing or two.
In the end, I realised that I could change my security question with my regular password, and then change the phone number with the new security question. All’s well that ends well.
How do You Deal with Security Questions?
I want to continue taking a high-security approach to my security questions. But as this anecdote shows, you do occasionally need to use them. With that in mind, we’d love to hear your best practices for security questions on accounts that you care about.
Do you store your answers in a similar way to your passwords, using high entropy to best security? When you are forced to use preselected questions do you answer honestly or make up nonsensical answers (and how do you remember what you answered from one account to the next)? When given the option to choose your own questions, what is your simple trick that ensures it all makes sense to you at a later date?
We’d love to hear your best-practice solutions in the comments. While you ponder those questions, one mystery will remain, however — the answer to the question that nobody knows: Chutney butler?