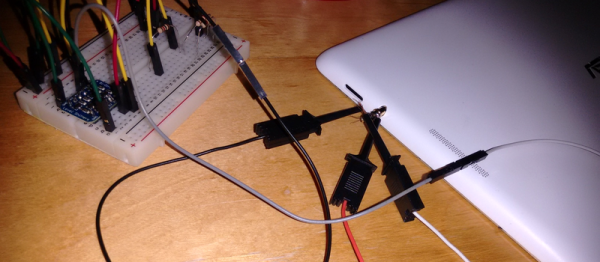
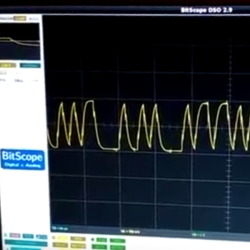
[ttsiodras] tells an epic tale of getting a custom Debian kernel installed on an Asus MemoPAD (ME103K) tablet. Skipping to the end of the saga, he discovers what looks like serial data coming out on the headphone jack when the system boots, but the signal was so distorted that he couldn’t simply interpret it. The solution turns out to be attaching a level-converter chip.
A level converter is a non-inverting amplifier, usually with a Schmitt trigger for immunity against noise. In this case, it acts like a “binarizer” — outputting a high voltage when the input rises above a threshold, and a low when it drops below. It’s the right part when you need to clean up a messy digital signal, and in this case works just fine because the capacitive distortion effects slow down both the leading and trailing edges of the signal, keeping the serial data’s timing intact.
That was the spoiler. If you want to read up on putting a custom Linux on an Android device, check out [ttsiodras]’s first post where he backs the machine up, and the second where he gets his custom kernel up and running. If you’re ever faced with an Android tablet that hasn’t been owned yet, or if you just have a DIY streak, this should help you get started.
Using the audio jack for serial is actually not uncommon, and discovering a serial terminal that listens at boot time is our favorite way to wedge a Linux OS into odd devices. So when you see a funny, distorted signal coming out at 115,200 baud, take a moment to clean its edges up and see what you’ve got.



 The specs I’m quoting come from the LG Optimus Exceed 2, which is currently available from Amazon in the USA for $20. The same package has been available for as little as $10 from retail stores in recent weeks. The Exceed 2 is just one of several low-cost Android prepaid phones on the market now, and undoubtedly the list will change. How to keep up with the current deals? We found an unlikely place. Perk farmers. Perk is one of those “We pay you to watch advertisements” companies. We’re sure some people actually watch the ads, but most set up “farms” of drone phones which churn through the videos. The drones earn the farmer points which can be converted to cash. How does this all help us? In order to handle streaming video, Perk farmers want the most powerful phones they can get for the lowest investment. Subreddits like
The specs I’m quoting come from the LG Optimus Exceed 2, which is currently available from Amazon in the USA for $20. The same package has been available for as little as $10 from retail stores in recent weeks. The Exceed 2 is just one of several low-cost Android prepaid phones on the market now, and undoubtedly the list will change. How to keep up with the current deals? We found an unlikely place. Perk farmers. Perk is one of those “We pay you to watch advertisements” companies. We’re sure some people actually watch the ads, but most set up “farms” of drone phones which churn through the videos. The drones earn the farmer points which can be converted to cash. How does this all help us? In order to handle streaming video, Perk farmers want the most powerful phones they can get for the lowest investment. Subreddits like 

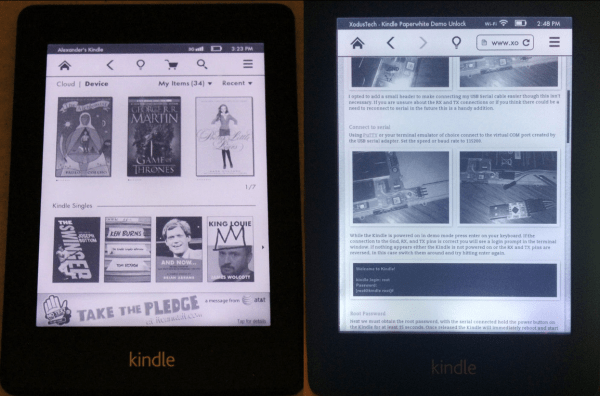
 The first step was to crack open the case and locate the serial port. [WarriorRocker] soldered a small three pin header to the pads to make it easier to work on his device as needed. He then connected the Kindle to his PC using a small serial to USB adapter. Pulling up the command prompt was as simple as running Putty and connecting to the correct COM port. If the wires are hooked up correctly, then it just takes a press of the enter key to pull up the login prompt.
The first step was to crack open the case and locate the serial port. [WarriorRocker] soldered a small three pin header to the pads to make it easier to work on his device as needed. He then connected the Kindle to his PC using a small serial to USB adapter. Pulling up the command prompt was as simple as running Putty and connecting to the correct COM port. If the wires are hooked up correctly, then it just takes a press of the enter key to pull up the login prompt.








