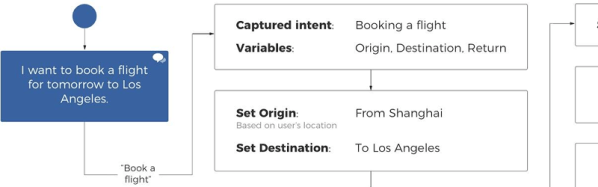
The last great hope for electronics manufactures is smart home assistants. The Alexas and Siris and OK Googles are taking over homes across the country. At its best, it’s HAL 9000, only slightly less homicidal. It will entertain your children, and you can order cat litter just by saying you want cat litter. This is the future, whether we like it or not.
In an attempt to capture the market, Amazon has released the Alexa Connect Kit. This is an Amazon-Echo-On-a-Chip — a piece of hardware that adds Alexa to microwaves, blenders, and whatever other bit of home electronics you can imagine.
The Alexa Connect Kit is the hardware behind Amazon’s efforts to allow developers easy integration with Alexa. The options for adding Alexa to a product up until now have been using Zigbee to connect an Echo Show or Echo Plus, or simply giving a device the ability to connect to an Echo through Bluetooth. The Alexa Connect Kit, however, is a pure hardware solution that puts Alexa in anything.
Unfortunately you can’t get one yet. Right now, the Alexa Connect Kit is just a preview, and if you want to get your hands on one — or get any specs on this bit of hardware — you’ll need to apply to the developer program. We’ve signed up and will share and juicy details that come our way as part of the program.
According to the Wall Street Journal (try Google referral link if you hit the pay wall), several companies are already working on integrating the Alexa Connect Kit into their existing product lines. Hamilton Beach and Procter & Gamble are both working on something, although the press doesn’t say what kind of device will now be loaded up with a voice assistant. Amazon, however, has a microwave using the technology that the owner can, “command the microwave to do things like defrost a half-pound of chicken, or set it up to automatically reorder a favorite type of popcorn on Amazon”.
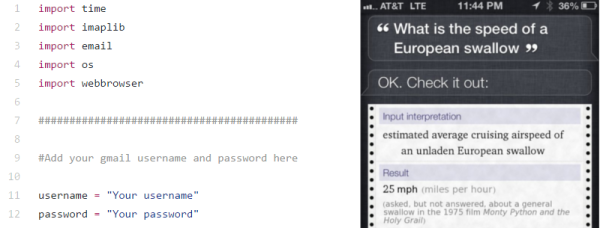
Despite the sparse details, this is relatively game-changing when it comes to the world of homebrew electronics. We’ve seen dozens of projects using hacked Raspberry Pis and other microcontrollers to at Alexa to hacked coffee machines, to shoot Nerf darts, and to control a projector. If you can actually get one of these Alexas-on-a-chip, all those projects could be done with one simple piece of hardware.








 That is just the experience of one hackspace, but it evidently does not end there. Every other day it seems that
That is just the experience of one hackspace, but it evidently does not end there. Every other day it seems that 








