Voice assistants are neat — they let us interface with computers without having to bother with touching them at all. Still, many decry the perceived privacy intrusion these devices present, as they’re always trucking data off to corporate servers for all kinds of opaque reasons. Building your own standalone assistant is a way to get around that, and that’s precisely what [Tristram] did.
 The build is based on an ESP32 Lyrat development board. Unlike most devboards, this one has two 3 watt audio outputs and mics on board, making it perfect for a build like this one. The Lyrat was paired with some NeoPixel LEDs and a pair of Dayton Audio 1.5″ speakers to enable it to interact with the user both audibly and visually.
The build is based on an ESP32 Lyrat development board. Unlike most devboards, this one has two 3 watt audio outputs and mics on board, making it perfect for a build like this one. The Lyrat was paired with some NeoPixel LEDs and a pair of Dayton Audio 1.5″ speakers to enable it to interact with the user both audibly and visually.
[Tristram] steps through not only how to set up the voice assistant, but also how to build it into a simple and attractive enclosure that won’t unduly stand out in the average house. The Lyrat simply has to be flashed with firmware that enables it to work as a voice aid with Home Assistant platform.
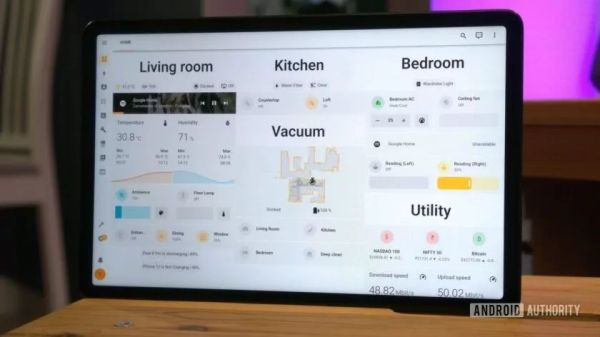
If you’re unfamiliar, Home Assistant is a smart home architecture that you can run yourself on your own hardware, without having everything live in the cloud of some murky corporation.
Home Assistant has grown in popularity in recent years as a less intrusive smarthome solution. You can even use it to monitor your hot tub! Video after the break.
Continue reading “Your Voice Assistant Doesn’t Have To Be Cloudy”