The Internet is a wild and wooly place where people can spout off about anything with impunity. If you sound like you know what you’re talking about and throw around a few bits of the appropriate jargon, chances are good that somebody out there will believe whatever you’re selling.
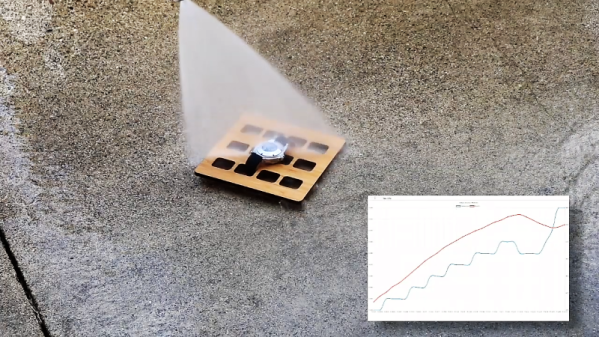
Case in point: those that purport that watches rated for 300-meter dives will leak if you wiggle them around too much in the shower. Seems preposterous, but rather than just dismiss the claim, [Kristopher Marciniak] chose to disprove it with a tiny wireless pressure sensor stuffed into a dive watch case. The idea occurred to him when his gaze fell across an ESP-01 module next to a watch on his bench. Figuring the two needed to get together, he ordered a BMP280 pressure sensor board, tiny enough itself to fit anywhere. Teamed up with a small LiPo pack, everything was stuffed into an Invicta dive watch case. A little code was added to log the temperature and pressure and transmit the results over WiFi, and [Kristopher] was off to torture test his setup.
The first interesting result is how exquisitely sensitive the sensor is, and how much a small change in temperature can affect the pressure inside the case. The watch took a simulated dive to 70 meters in a pressure vessel, which only increased the internal pressure marginally, and took a skin-flaying shower with a 2300-PSI (16 MPa) pressure washer, also with minimal impact. The video below shows the results, but the take-home message is that a dive watch that leaks in the shower isn’t much of a dive watch.
Hats off to [Kristopher] for doing the work here. We always love citizen science efforts such as this, whether it’s hardware-free radio astronomy or sampling whale snot with a drone.
Continue reading “Torturing An Instrumented Dive Watch, For Science”