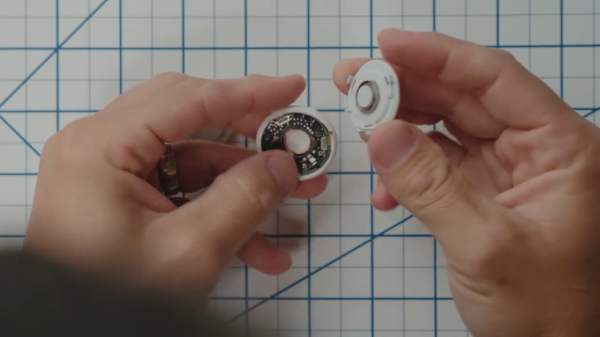
Psst! Hey kid! Want to reverse-engineer some iPhones? Well, did you know that modern iPhones use PCIe, and specifically, NVMe for their storage chips? And if so, have you ever wondered about sniffing those communications? Wonder no more, as this research team shows us how they tapped them with a flexible printed circuit (FPC) BGA interposer on an iPhone 6S, the first iPhone to use NVMe-based storage.
The research was done by [Mohamed Amine Khelif], [Jordane Lorandel], and [Olivier Romain], and it shows us all the nitty-gritty of getting at the NVMe chip — provided you’re comfortable with BGA soldering and perhaps got an X-ray machine handy to check for mistakes. As research progressed, they’ve successfully removed the memory chip dealing with underfill and BGA soldering nuances, and added an 1:1 interposer FR4 board for the first test, that proved to be successful. Then, they made an FPC interposer that also taps into the signal and data pins, soldered the flash chip on top of it, successfully booted the iPhone 6S, and scoped the data lines for us to see.
This is looking like the beginnings of a fun platform for iOS or iPhone hardware reverse-engineering, and we’re waiting for further results with bated breath! This team of researchers in particular is prolific, having already been poking at things like MITM attacks on I2C and PCIe, as well as IoT device and smartphone security research. We haven’t seen any Eagle CAD files for the interposers published, but thankfully, most of the know-how is about the soldering technique, and the paper describes plenty. Want to learn more about these chips? We’ve covered a different hacker taking a stab at reusing them before. Or perhaps, would you like to know NVMe in more depth? If so, we’ve got just the article for you.
We thank [FedX] for sharing this with us on the Hackaday Discord server!






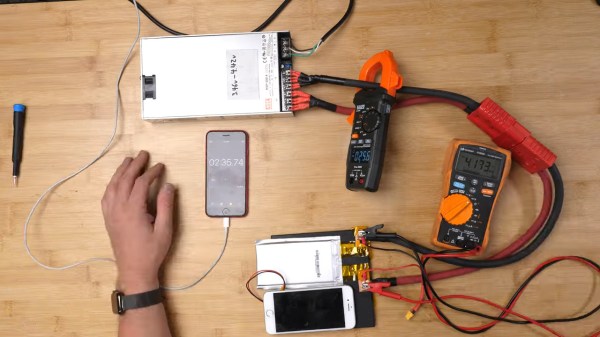
 What people commonly encounter is that charging speed depends on the charger involved, but even one hundred chargers in parallel won’t speed up this iPhone’s charging rate, so what’s up? First off, the phone’s charger chip and the battery’s BMS will both limit charging current, so for experiment purposes, those had to be bypassed. First attempt was using a hefty DC power supply with the original cell, and, unsatisfied with the lack of fire and still relatively slow charging, [Scotty] decides to up the ante.
What people commonly encounter is that charging speed depends on the charger involved, but even one hundred chargers in parallel won’t speed up this iPhone’s charging rate, so what’s up? First off, the phone’s charger chip and the battery’s BMS will both limit charging current, so for experiment purposes, those had to be bypassed. First attempt was using a hefty DC power supply with the original cell, and, unsatisfied with the lack of fire and still relatively slow charging, [Scotty] decides to up the ante.









