Air quality has become a hot topic in recent years. [Ryan Stout] was interested in improving it in his camper van, and set about doing something about it. His solution was an automated system that provided cleaner air and better comfort to boot.
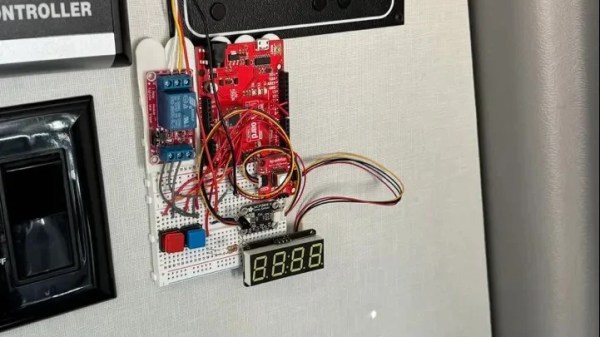
The concept was simple. [Ryan]’s system is based on an Arduino clone, and uses a SparkFun SCD40 as a CO2 sensor, and an MCP9808 for temperature. When the system detects excess carbon dioxide levels, it opens the MaxxAir fan in the camper by triggering it with an infrared signal. Similarly, when it detects excessively low temperatures inside the van, it kicks on a diesel furnace for heating. In a neat addition, to avoid the fan sucking in exhaust fumes, it also closes the fan in order to avoid exhaust fumes entering the camper unnecessarily. All the hardware was then wrapped up in a simple 3D printed enclosure.
With this setup, [Ryan] has managed to cut the buildup of CO2 in his camper at night, and he credits this with reducing morning headaches when he’s out in the camper. We’d call that a win, to say nothing of the additional comfort created by the automatically-controlled heater! If you’re interested in something similar for your home HVAC system, we’ve got you covered.