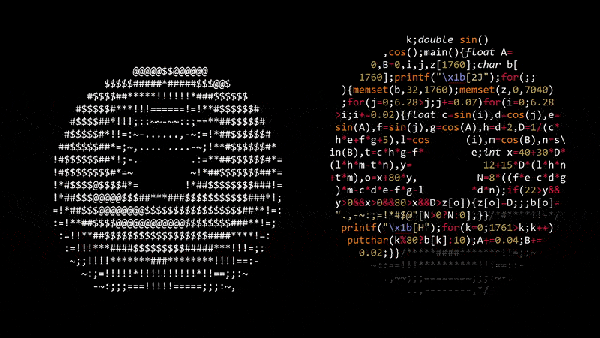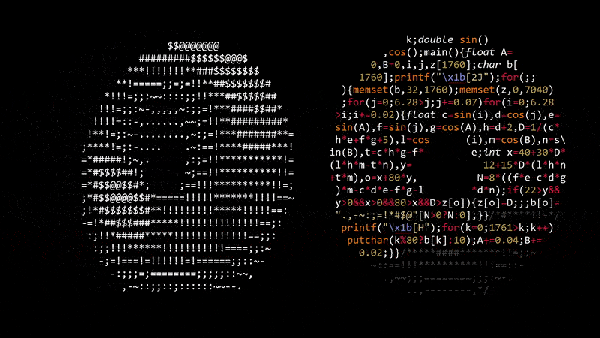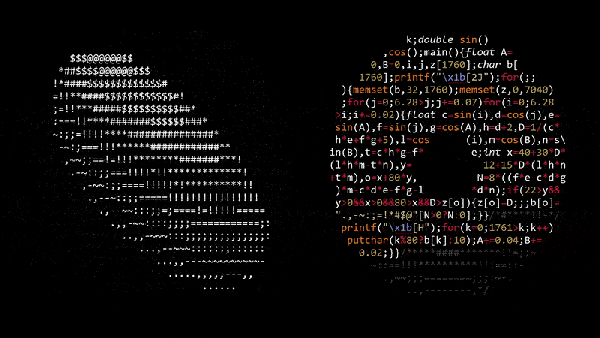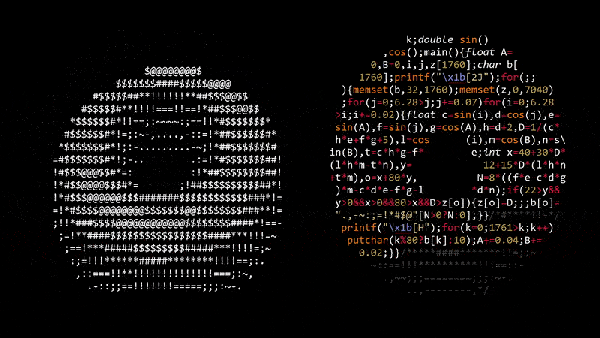
In case you grow tired of clear-written, understandable code, obfuscation contests provide a nice change of scenery, and trying to make sense of their entries can be a fun-time activity and an interesting alternative to the usual brainteasers. If we ever happen to see a Simpsons episode on the subject, [Andy Sloane] has the obvious candidate for a [Hackerman Homer] entry: a rotating ASCII art donut, formatted as donut-shaped C code.
The code itself actually dates back to 2006, but has recently resurfaced on Reddit after [Lex Fridman] posted a video about it on YouTube, so we figured we take that chance to give some further attention to this nifty piece of art. [Andy]’s blog article goes in all the details of the rotation math, and how he simply uses ASCII characters with different pixel amounts to emulate the illumination. For those who prefer C over mathematical notation, we added a reformatted version after the break.
Sure, the code’s donut shape is mainly owed to the added filler comments, but let’s face it, the donut shape is just a neat little addition, and the code wouldn’t be any less impressive squeezed all in one line — or multiple lines of appropriate lengths. However, for the actual 2006 IOCCC, [Andy] took it a serious step further with his entry, and you should definitely give that one a try. For some more obfuscated shell animations, check out the fluid dynamics simulator from a few years back, and for a more recent entry, have a look at the printf Tic Tac Toe we covered last month.