One of the most popular futurist tropes of the 20th century was the video intercom. Once this technology was ready, it would clearly become a mainstay of modern living overnight. Our lived reality is however somewhat different. For [MisterM], that simply wouldn’t do, so he set about producing a retro-themed video doorbell that is sure to be the envy of the neighbourhood.
Not one to settle for second best, [MisterM] wanted to focus on quality in video and sound. A Microsoft LifeCam 3000HD handles video and audio capture, with a Raspberry Pi 3B+ providing plenty of grunt to run the show. The Pimoroni pHAT BEAT add-on provides audio output. It’s all integrated into a 1980s vintage intercom, which is painted a deep shade of maroon for an extra classy look. Further parts are integrated into a classic Sony tape deck, with LEDs shining out from under the cassette door for added visual appeal.
The doorbell works by making calls to Google Duo, which allows the user to answer the door from anywhere in the house, or indeed – anywhere with an Internet connection! [MisterM] reports this has already proved useful for communicating with couriers delivering packages to the house. There’s also a standard wireless doorbell and chime integrated into the unit which alerts those within the house in the usual way.
It’s a project that is both highly functional and looks particularly swish. Integrating new brains into old-school enclosures is a great way to give your project a cool look. These aircraft surplus clocks are a great example. Video after the break.
Continue reading “Video Doorbell Focuses On Quality, Aesthetic”


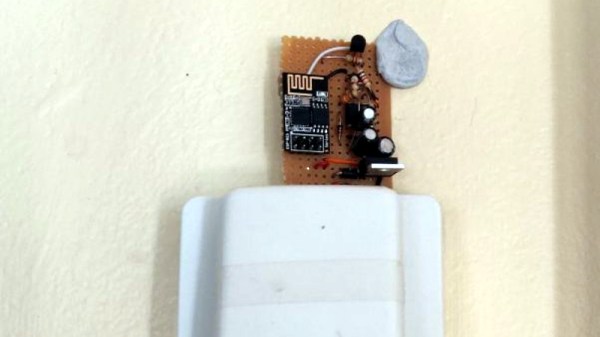
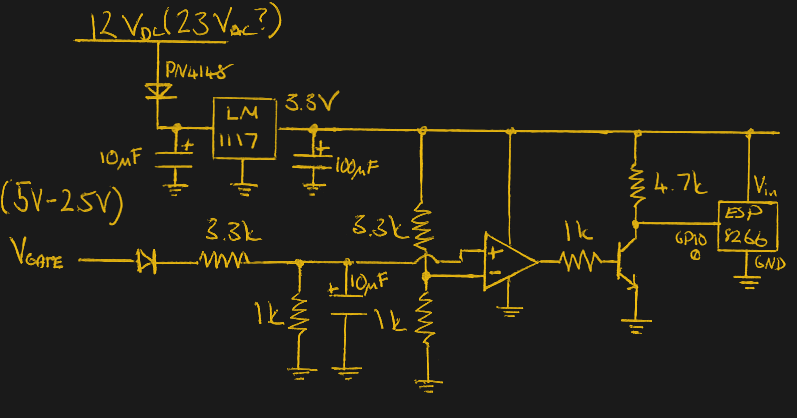
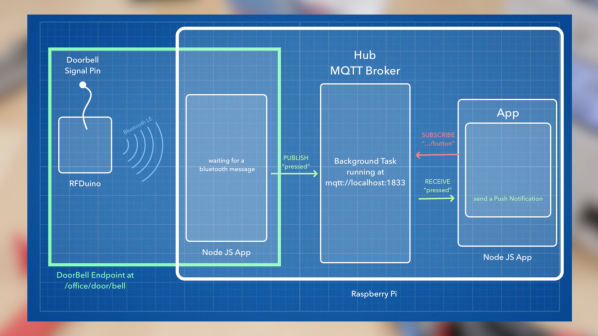

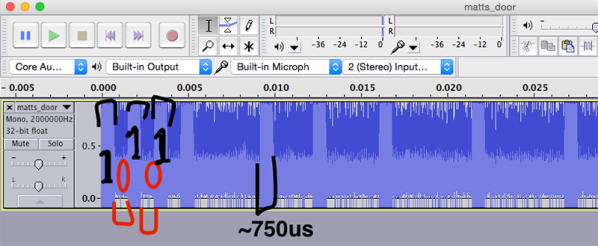
 The design is pretty simple – an ATMega328P to snoop on the analog phone ringer in the apartment when the intercom call button is pushed, and a relay wired in parallel with the door switch to buzz him in. For added security, the microcontroller detects the pattern of button presses and prevents unwanted guests from accessing the lobby. Things got really fun when [Paweł] added a PCM audio module to play random audio clips through the intercom. As you can see in the video below, an incorrect code might result in a barking dog or a verbal put-down. But [Paweł] earns extra points for including the Super Mario Bros sound clip and for the mashup of the “Imperial March” with “The Girl from Ipanema”.
The design is pretty simple – an ATMega328P to snoop on the analog phone ringer in the apartment when the intercom call button is pushed, and a relay wired in parallel with the door switch to buzz him in. For added security, the microcontroller detects the pattern of button presses and prevents unwanted guests from accessing the lobby. Things got really fun when [Paweł] added a PCM audio module to play random audio clips through the intercom. As you can see in the video below, an incorrect code might result in a barking dog or a verbal put-down. But [Paweł] earns extra points for including the Super Mario Bros sound clip and for the mashup of the “Imperial March” with “The Girl from Ipanema”.