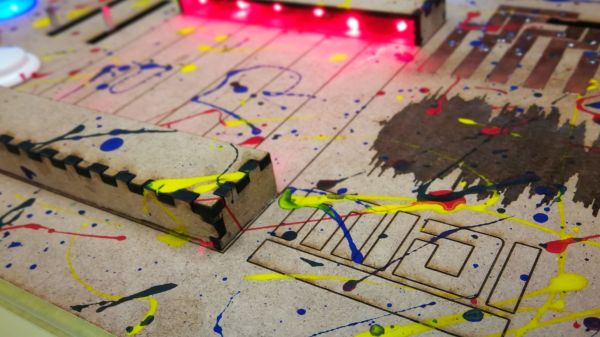
Do you ever peer into the void…of your hardware scrap box? It may be a wonderland of parts with near-infinite potential, and they just need to be assembled and depending on what you hoard, programmed. Access to a laser engraver doesn’t hurt either. The stuff in [Mr. Sobolak]’s bin is cooler than average, at least by Hackaday writer standards. His sound palette project is a wild mixture of interfaces, hardware, channels, and color. There are arcade pushbuttons, slider potentiometers, rotary potentiometers, miniature laser harp, touch piano, and drum pads which earns the title of junk box build extraordinaire.
Under the hood, we find the usual copper tape, wire and solder connecting operators to a Teensy 3.2. In the more esoteric part of the BOM, we find some fancy SoftPots which look like great fun to play. All the code is linked in the Instructable, but there is absolutely no reason to make an exact copy. MIDI is from the 80s and libraries abound for this protocol so the building may be the hardest part of making an interface that fits your character. Some of the techniques in the Instructable may help you, like how to connect a piezo element so it can read something lighter than a wrecking ball or the laser harp roughly the size of your palm.
We are not short of MIDI interfaces if you are thinking of making your own or be truly random.