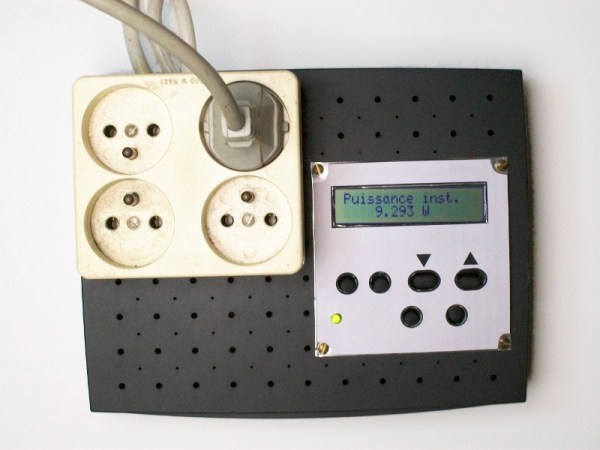
[Renaud] built a AC power meter from scratch. While commercial power meters like the Kill A Watt are available [Renaud’s] build gives an interesting insight into the methods used.
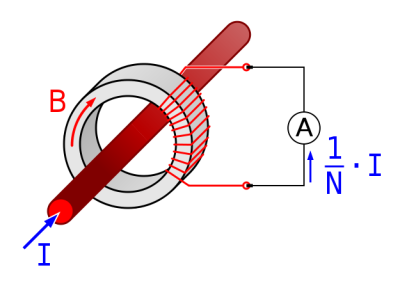 At the heart of [Renaud’s] design lie two sense transformers. The first is a typical voltage stepdown transformer. This brings the AC line voltage down to +/- 10V, which is more amenable to digital sampling. The second is a current sense transformer. In current transformers the primary is typically a single wire (the AC line in this case) passing through the middle of a ring (see the picture to the right from wikipedia). The secondary is wrapped round the ring. When the secondary coil is shorted a current in the primary wire/coil induces a current in the secondary coil.
At the heart of [Renaud’s] design lie two sense transformers. The first is a typical voltage stepdown transformer. This brings the AC line voltage down to +/- 10V, which is more amenable to digital sampling. The second is a current sense transformer. In current transformers the primary is typically a single wire (the AC line in this case) passing through the middle of a ring (see the picture to the right from wikipedia). The secondary is wrapped round the ring. When the secondary coil is shorted a current in the primary wire/coil induces a current in the secondary coil.
In practice, the voltage drop across a low value resistor is used to detect the current in the secondary. Clamp meters use this principle to make non-contact current measurements. Other power meters often use hall effect sensors for current measurements. It will be interesting to see how these methods compare when [Renaud] benchmarks this build.
[Renaud] takes the voltage and current readings from these transformers and samples them with a PIC in order to calculate power. As the AC voltage is periodic [Renaud] uses a method similar to Equivalent Time Sampling (ETS) to combine waveforms from multiple cycles and increase the effective sample rate.
Great stuff [Renaud]!


 The build starts with the slab sides of the truck. The basic outline is cut into a piece of lumber which is then split with a handsaw to create a left and a right side. From there, [Headquake137’s] uses a Dremel to carve away anything that doesn’t look like a 1977 F100. He adds pieces of wood for the roof, hood, tailgate, and the rest of the major body panels. Small details like the grille and instrument panel are created with white polystyrene sheet, an easy to cut material often used by train and car modelers.
The build starts with the slab sides of the truck. The basic outline is cut into a piece of lumber which is then split with a handsaw to create a left and a right side. From there, [Headquake137’s] uses a Dremel to carve away anything that doesn’t look like a 1977 F100. He adds pieces of wood for the roof, hood, tailgate, and the rest of the major body panels. Small details like the grille and instrument panel are created with white polystyrene sheet, an easy to cut material often used by train and car modelers.