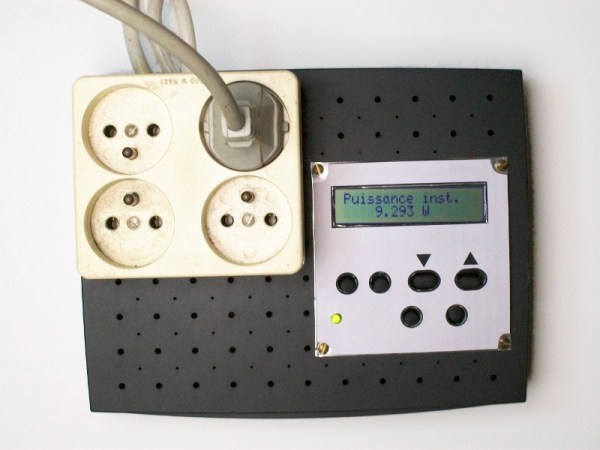
If someone lobs a grenade, it’s fair to expect that something unpleasant is going to happen. Tear gas grenades are often used by riot police to disperse an unruly crowd, and the military might use a smoke grenade as cover to advance on an armed position, or to mark a location in need of an airstrike. But some gas grenades are meant to help, not hurt, like this talking gas-sensing grenade that’s a 2015 Hackaday Prize entry.
Confined space entry is a particularly dangerous aspect of rescue work, especially in the mining industry. A cave in or other accident can trap not only people, but also dangerous gasses, endangering victims and rescuers alike. Plenty of fancy robots have been developed that can take gas sensors deep into confined spaces ahead of rescuers, but [Eric William] figured out a cheaper way to sniff the air before entering. An MQ2 combination CO, LPG and smoke sensor is interfaced to an Arduino Nano, and a 433MHz transmitter is attached to an output. A little code measures the data from the sensors and synthesizes human voice readings which are fed to the transmitter. The whole package is stuffed into a tough, easily deployed package – a Nerf dog toy! Lobbed into a confined space, the grenade begins squawking its readings out in spoken English, which can be received by any UHF handy-talkie in range. [Eric] reports in the after-break video that he’s received signals over a block away – good standoff distance for a potentially explosive situation.
Continue reading “Hackaday Prize Entry: Gas Grenade Helps Instead Of Exploding”




 The build starts with the slab sides of the truck. The basic outline is cut into a piece of lumber which is then split with a handsaw to create a left and a right side. From there, [Headquake137’s] uses a Dremel to carve away anything that doesn’t look like a 1977 F100. He adds pieces of wood for the roof, hood, tailgate, and the rest of the major body panels. Small details like the grille and instrument panel are created with white polystyrene sheet, an easy to cut material often used by train and car modelers.
The build starts with the slab sides of the truck. The basic outline is cut into a piece of lumber which is then split with a handsaw to create a left and a right side. From there, [Headquake137’s] uses a Dremel to carve away anything that doesn’t look like a 1977 F100. He adds pieces of wood for the roof, hood, tailgate, and the rest of the major body panels. Small details like the grille and instrument panel are created with white polystyrene sheet, an easy to cut material often used by train and car modelers.

















