If you are fascinated by stories you read on sites like Hackaday in which people reverse engineer wireless protocols, you may have been tempted to hook up your RTL-SDR stick and have a go for yourself. Unfortunately then you may have encountered the rather steep learning curve that comes with these activities, and been repelled by a world with far more of the 1337 about it than you possess. You give up after an evening spent in command-line dependency hell, and move on to the next thing that catches your eye.
You could then be interested by [Jopohl]’s Universal Radio Hacker. It’s a handy piece of software for investigating unknown wireless protocols. It supports a range of software defined radios including the dirt-cheap RTL-SDR sticks, quickly demodulates any signals you identify, and provides a whole suite of tools to help you extract the data they contain. And for those of you scarred by dependency hell, installation is simple, at least for this Hackaday scribe. If you own an SDR transceiver, it can even send a reply.
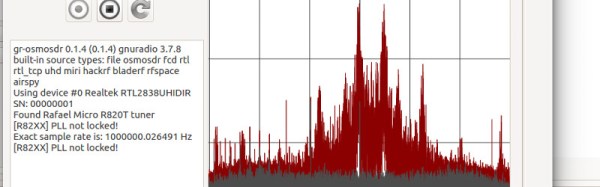
To prove how straightforward the package is, we put an RTL stick into a spare USB port and ran the software. A little investigation of the menus found the spectrum analyser, with which we were able to identify the 433 MHz packets coming periodically from a wireless thermometer. Running the record function allowed us to capture several packets, after which we could use the interpretation and analysis screens to look at the binary stream for each one. All in the first ten minutes after installation, which in our view makes it an easy to use piece of software. It didn’t deliver blinding insight into the content of the packets, that still needs brain power, but at least if we were reverse engineering them we wouldn’t have wasted time fighting the software.
We’ve had so many reverse engineering wireless protocol stories over the years, to pick only a couple seems to miss the bulk of the story. However both this temperature sensor and this weather station show how fiddly it can be without a handy software package to make it easy.
Via Hacker News.