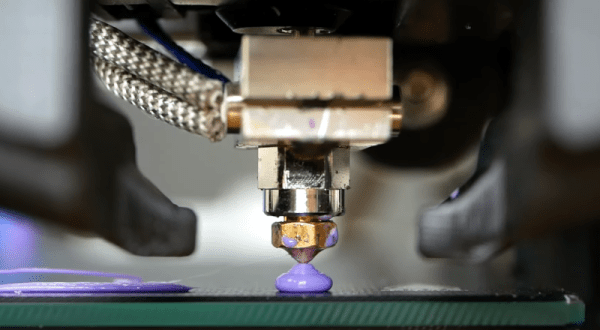
A lot of people want to print faster. Maybe they don’t like to wait, or they need to print a lot of things. Maybe it is just human nature to want to push things to go faster. The problem is, if you move filament too fast it may not have time to melt inside the hot end. To combat that, some people install a “volcano” — a larger heat block that takes a special longer nozzle. The melt zone is longer so there is more time for the filament to liquefy before shooting out of the nozzle. This is also a problem if you are using a very large nozzle size. But what if you don’t have one of these special hot ends? According to [Stefan], you can use a normal hotend with a volcano-style nozzle just by adding some common nuts. You can see the explanation in the video, below.
The idea came from a few commercial offerings that allow converting between different-sized melt zones. Some of these use the same idea. But, if you are familiar with [Stefan’s] videos, you know he tested the results thoroughly. The tests reveal that a standard V6-style hotend can handle rates of just over 9.8mm/second. with a 0.4mm nozzle at 210C and is usable beyond that. A true volcano hotend. starts deviating from the ideal at about 15mm/second and, also, is usable at even higher rates. But what about just using a long nozzle in a regular block with or without the nuts?
Continue reading “Want Faster Extrusion But Don’t Have A Volcano? Nuts!”