For plenty of media center PCs, home theaters, and people with a simple TV and a decent audio system, the standard speaker setup now is 5.1 surround sound. Left and right speakers in the front and back, with a center speaker and a subwoofer. But the 5.1 setup wasn’t always the standard (and still isn’t the only standard); after stereo was adopted mid-century, audio engineers wanted more than just two channels and briefly attempted a four-channel system called quadrophonic sound. There’s still some media from the 70s that can be found that is built for this system, such as [Alan]’s collection of 8-track tapes. These tapes are getting along in years, so he built a quadrophonic 8-track replica to keep the experience alive.
The first thing needed for a replica system like this is digital quadrophonic audio files themselves. Since the format died in the late 70s, there’s not a lot available in modern times so [Alan] has a dedicated 8-track player connected to a four-channel audio-to-USB device to digitize his own collection of quadrophonic 8-track tapes. This process is destructive for the decades-old tapes so it is very much necessary.
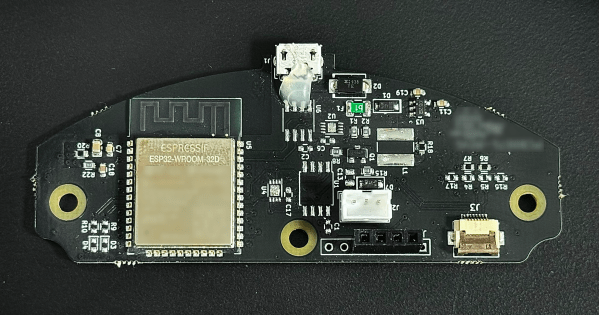
With the audio files captured, he now needs something to play them back with. A Raspberry Pi is put to the task, but it needs a special sound card in order to play back the four channels simultaneously. To preserve the feel of an antique 8-track player he’s cannibalized parts from three broken players to keep the cassette loading mechanism and track indicator display along with four VU meters for each of the channels. A QR code reader inside the device reads a QR code on the replica 8-track cassettes when they are inserted which prompts the Pi to play the correct audio file, and a series of buttons along with a screen on the front can be used to fast forward, rewind and pause. A solenoid inside the device preserves the “clunk” sound typical of real 8-track players.
As a replica, this player goes to great lengths to preserve the essence of not only the 8-track era, but the brief quadrophonic frenzy of the early and mid 70s. There’s not a lot of activity around quadrophonic sound anymore, but 8-tracks are popular targets for builds and restorations, and a few that go beyond audio including this project that uses one for computer memory instead.
Continue reading “Recreating The Quadrophonic Sound Of The 70s”